A new ransomware campaign has affected atleast 3 Russian media companies. Fontanka, Interfax are among the affected companies. The ransomware is named Bad Rabbit. The malware is delivered as fake flash installer, it uses the SMB protocol to check hardcoded credentials. Bad Rabbit does not employ any exploits to gain execution or elevation of privilege. The Ukrainian computer emergency agency CERT-UA has issued an alert incident and mentioned that Odessa airport and Kiev subway were also affected. It is unclear whether this alert is regarding Bad Rabbit but they suspect that it may be due to the start of a new wave of cyberattacks.
Infection
As mentioned earlier the ransomware is delivered as a drive-by attack from compromised websites. File named “install_flash_player.exe” is dropped by the website, the user needs to manually execute it. It is a bootkit based ransomware similar to Petya/NotPetya. Upon execution it encrypts the files on the target machine and installs its own bootloader in MBR and schedules a reboot. After the system reboots it displays the ransom note to the user, the OS does not boot.
Upon execution the file tries to gain privilege via the standard UAC prompt. After acquiring the privileges it creates a file under “C:\Windows\infpub.dat“. This file is executed using rundll32. infpub.dat drops dispci.exe under C:\Windows, this executable is responsible for encrypting the files and modifying the boot-loader, it is derived from DiskCryptor an open sourced full disk encryption system for Windows. The ransomware schedules tasks with names rhaegal, drogon, viserion (Game of Throne references). rhaegal to reboot the system and drogon to execute dispci.exe at system start up.
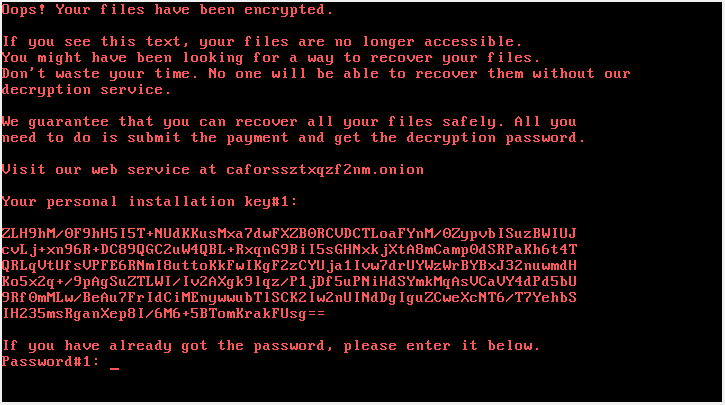
Each infected machine is provided with a unique key or a bitcoin address. The user needs to connect to a hidden Tor service caforssztxqzf2nm[.]onion, to pay the ransom. The website is titled BAD RABBIT hence the name of the ransomware . The user enters their public key or bitcoin address allotted by the ransomware. It also shows a timer counting down from 40 hours after which the price decryption will increase. Currently the ransom is 0.05 bitcoin which is valued at $284.00 as of 24-Oct-17 20:10:27 UTC. The ransomware encrypts over 100 different file extensions including .ppt,.pptx,.doc,docx etc.
Mititgation
Please update your End point solution with the latest signature set, Also make sure the machines on the network are patched with the latest fixes from Microsoft. You can scan your network with QID 1043 to detect machines infected with the Bad Rabbit.
QID Detection Logic:
The QID checks for the presence of %windir%\dispci.exe. Apart from the file the QID also tries to detect scheduled tasked named- drogon, rhaegal, viserion. The QID will flag if anyone of these artifacts are present. Please note that this QID is effective for machines that have not yet rebooted after the initial infection cycle.
Additional mitigation steps:
– Disable WMI service if possible
– Block the execution of C:\windows\infpub.dat and C:\Windows\cscc.dat.
Qualys IOCs
install_flash_player.exe [SHA256]: 630325cac09ac3fab908f903e3b00d0dadd5fdaa0875ed8496fcbb97a558d0da
C:\Windows\dispci.exe [SHA256]: 8ebc97e05c8e1073bda2efb6f4d00ad7e789260afa2c276f0c72740b838a0a93
C:\windows\infpub.dat [SHA256]: 579fd8a0385482fb4c789561a30b09f25671e86422f40ef5cca2036b28f99648
C:\windows\cscc.dat [SHA256]:8d63e37aa74ca33a926bec7c7aa8fda0f764ffbb20e8f64bb9c3999b5975f9a6
Please continue to follow ThreatProtect for more details about Bad Rabbit.
References
CERT-UA
Bad Rabbit: New ransomware wave hitting RU & UA [InfoSec Handler]
Bad Rabbit: A new ransomware epidemic is on the rise
Bad Rabbit ransomware
New Ransomware ‘Bad Rabbit’ Spreading Quickly Through Russia and Ukraine
Kiev metro hit with a new variant of the infamous Diskcoder ransomware