Petya is not a new player in the ransomware world. It has multiple versions and was delivered to target machines as part of exploit kit campaigns and as malicious email attachments. The latest versions of petya seems to be spreading via the SMBv1 vulnerabilities (CVE-2017-0144 and CVE-2017-0145) in the Windows operating system. This behavior is similar to the WannaCry ransomware.
Infection Cycle
One of the initial infection vector for Petya was found to be a modified update file for M.E.Doc a Ukrainian tax accounting application. Upon execution Petya uses a lightweight version of mimkatz to obtain the password of the infected machine. With the credentials in hand it obtains all hosts on the network on TCP port 139 and 445. Once it has a valid target it copies a binary and tries to execute it using PSEXEC or WMIC. Petya is capable of lateral movement using EternalBlue and EternalRomance SMB exploits.
Petya also checks if certain processes are running, it generates a key with the process name, based on these checks the ransomware alters its execution cycle. It also checks if the dll is already present in the windows folder.
Encryption
Petya targets the MBR (Master Boot Record) record if it has SeDebugPrivilege, it over writes the MBR with a custom boot loader that loads the encryption module. This module encrypts the Master File Table (MFT), which renders the file system un-readable. On reboot the boot-loader presents a chkdsk styled interface showing that it is repair disk errors, but it is actually encrypting the files on the disk. It targets all file and folder in fixed drives excluding C:\Windows. The malware does not append a new extension to encrypted files.
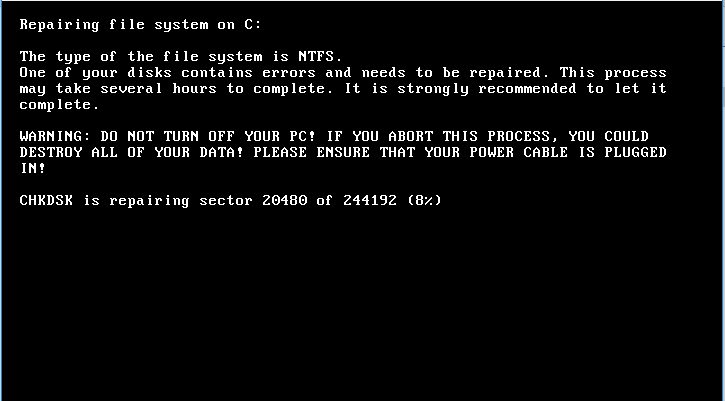
After this step it displays the ransom note and instructions for obtaining the decryption key. As per MSRC it also clears the System, Setup, Security, Application event logs and deletes NTFS journal info.
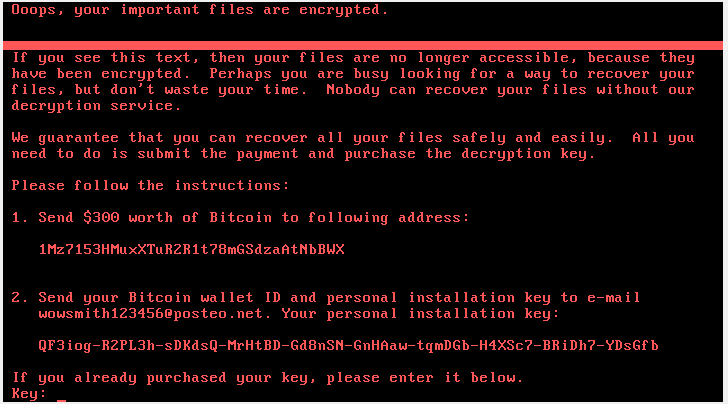
The email address mentioned in the ransom note has been disabled by the providers, this means payment messages will not be delivered. According to news Petya is targeting businesses in Ukraine, Russia and Western Europe.
Mitigation
- Apply the latest patches for Windows. Scan your network with Qualys to detect vulnerable machines.
- If patches cannot be applied for some reason MRSC has suggests workaround to address the SMB vulnerabilities.
- We request organizations to scan their networks with QID 1037 to detect infected machines. The QID in question will be only effective if the ransomware has not reached the encryption phase in its infection cycle, which is before a system reboot.
- Use the Windows AppLocker feature to disable the execution of files named perfc.dat and PSExec.exe.
- Disable WMIC.
- Disable SMBv1.
- Block TCP Port 445 at the perimeter.
- Make sure systems are running up to date HIDS applications.
- Enforce secure password policy.
- Disable the admin$ share through group policy.
- There are reports in social media about a killswitch by creating a file under “C:\\Windows\perfc.dat”. This is not entirely reliable. We urge organizations to use a fully updated Anti-Virus solution to protect machines from Petya.
Technical Details
Petya utilizes executables with the following hashes:
- file.hash.md5: 71b6a493388e7d0b40c83ce903bc6b04
- file.hash.md5: 7e37ab34ecdcc3e77e24522ddfd4852d
Please continue to follow ThreatProtect for more information about Petya.
References:
Petya— Enhanced WannaCry ?
Petya: Hybrid Analysis
CERT.be