WannaCry is malware with a worm+ransomware characteristics as such it is a blended threat. Initial news of attacks were provided by Telefonica in Spain, the malware was able to spread to networks in the National Health Service (NHS) and has infected at least 16 Hospitals, followed by many other incidents across the world. The ransomware uses the ETERNALBLUE exploit to spread to other vulnerable machines. This post details the initial stages in the ransomware’s execution leading upto the start of its encryption phase. Below are the file details of the sample used in this analysis.
| File Name : | C:\Users\IEUser\Downloads\WannaCry.exe |
| Internal Name: | lhdfrgui.exe |
| FileDescription : | Microsoft® Disk Defragmenter |
| File Type : | Portable Executable 32 |
| File Size: | 3.55MB (3723264 bytes) |
| MD5: | DB349B97C37D22F5EA1D1841E3C89EB4 |
| SHA-1 | E889544AFF85FFAF8B0D0DA705105DEE7C97FE26 |
The file is a PE32 executable built in C++. Upon execution the malware checks for reach-ability to “http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com” if it fails the execution continues and if it succeeds it will terminate the process.
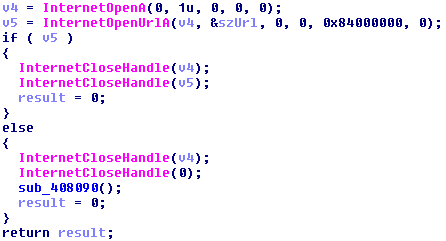
If v5 is NULL then it proceeds to call subroutine ‘sub_408090’. There are confirmed reports by researchers that they are other variants in wild which check for the other domains.
iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com
ifferfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com
iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]test
iuqssfsodp91fjaposdfjhgosurijfaewrwergwea[.]com
ayy1maotjhsstasdfasdfasdfasdfasdfasdfasdf[.]com
The .test is a reserved by the Internet Engineering Task Force and not be used a top level domain. These checks for domains could be an evasion method used to detect sandboxes or lab setups where common internet services are simulated. Most of theses domains apart from .test have been sinkholed to prevent further spread of infection.
Going back to our analysis the subroutine “sub_408090”, finds the path to itself and checks if it has any command line arguments.
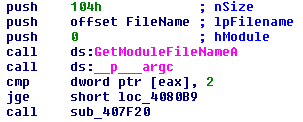
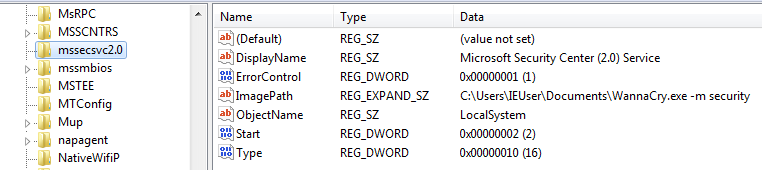
If there are no command line arguments. It tries to open a connection to the active services database on the machine with SC_MANAGER_ALL_ACCESS. With the connection handle to the database it attempts to start a service named “Microsoft Security Center (2.0) Service” with the executable path pointing to “C:\Users\IEUser\Documents\WannaCry.exe -m security”.
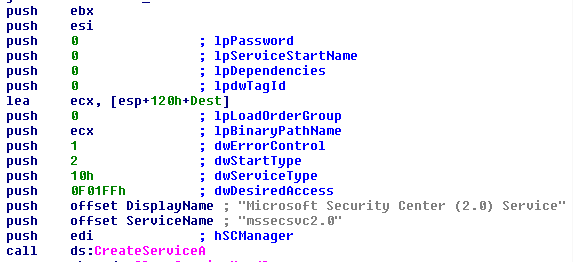
This creates a service object which when started will have
- SERVICE_ALL_ACCESS
- SERVICE_AUTO_START
- Executable pointing to “C:\Users\IEUser\Documents\WannaCry.exe -m security”
This action adds the corresponding registry when the service starts. Notice the command line argument “-m security”.
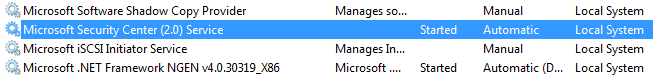
If the ransomware detects that they are >=2 command line arguments the executable tries to start this service directly.The ransomware will continue execution Irrespective of the success of this service start sequence. Moving on it obtains a handle to kernel32.dll and resolves the process address for CreateProcessA, CreateFileA,WriteFile,CloseHandle, a tell-tale signs of file operation and may be try to spawn a new process.
First it tries to find a resource block from within its PE header.
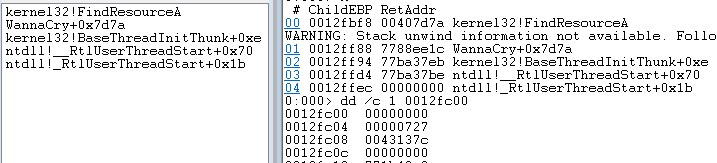
From the stack trace above we can see that it is trying find a resource block named 727h(1831 base 10) within resource type/block “R”. We can verify this manually.
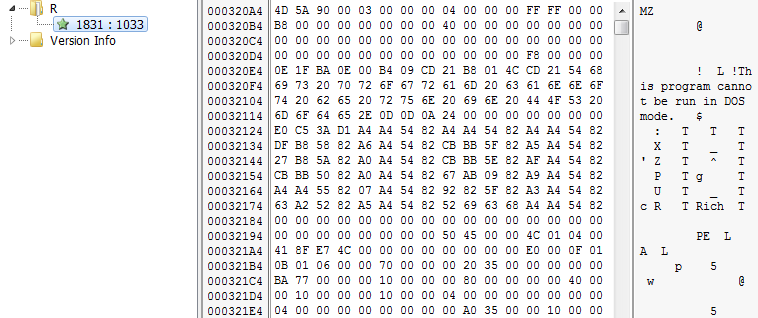
Things are becoming very interesting now. It appears that the an executable is embedded within the resource section of the main executable. The embedded file has a DOS executable header followed by a PE header. The subroutine obtains a lock on the resource block and writes it to “C:\WINDOWS\tasksche.exe”.
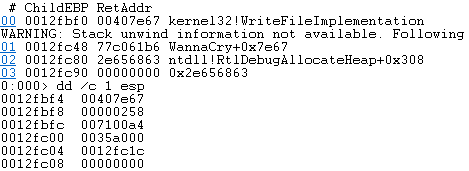
In image above we can see the call stack leading up to the WriteFile function call. The value 0x258 is the handle for the “tasksche.exe”.
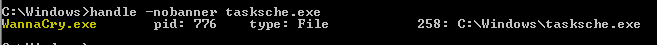
And the contents to be written are stored at 0x007100a4. The total size of the executable is 3514368 bytes.
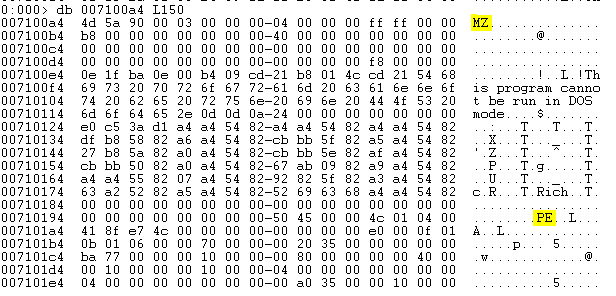
Now that the executable is created, it will create a process for “tasksche.exe” which will encrypt the target machine.
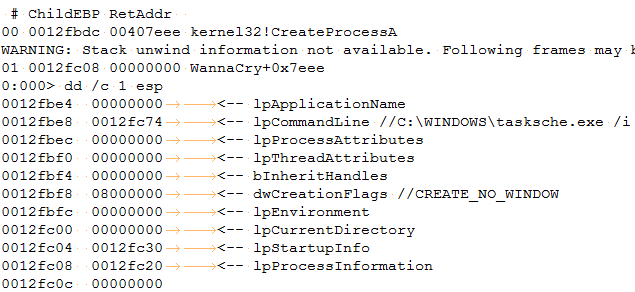
Upon execution “tasksche.exe” will further spawn addition processes for encrypting files on the target machine.
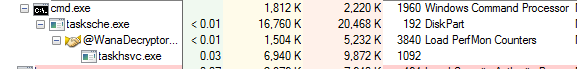
Notice the “/i” command line argument for “tasksche.exe”, We will continue our analysis to find out what it does.
Summary:
The main ransomware executable is a dropper which configures the system for the encrypting executable “taskche.exe”. The executable in question is embedded within the resource section, the file, and is used to create “taskche.exe”. The malware achieves persistence by starting a system level service which start automatically. Please continue follow us on ThreatProtect for more coverage on WannaCry.