Summary:
This time an out-of-bounds read vulnerability was observed in in macOS Catalina 10.15.3. that leads to memory leakage vulnerability.
Description:
The Vulnerability involved in this exploit is in the processing code of SDP (Service Discovery Protocol) data frames. This section briefly introduces the SDP frame, as follows:

Image Source: 360
The first byte PDU field indicates the SDP request or response message. PDU = 2/4/6 indicates SDP Request, and PDU = 0/1/3/5 indicates SDP Response. The Parameter Length field indicates the length of the payload. You can use wireshark to capture and analyze the packets as follows:
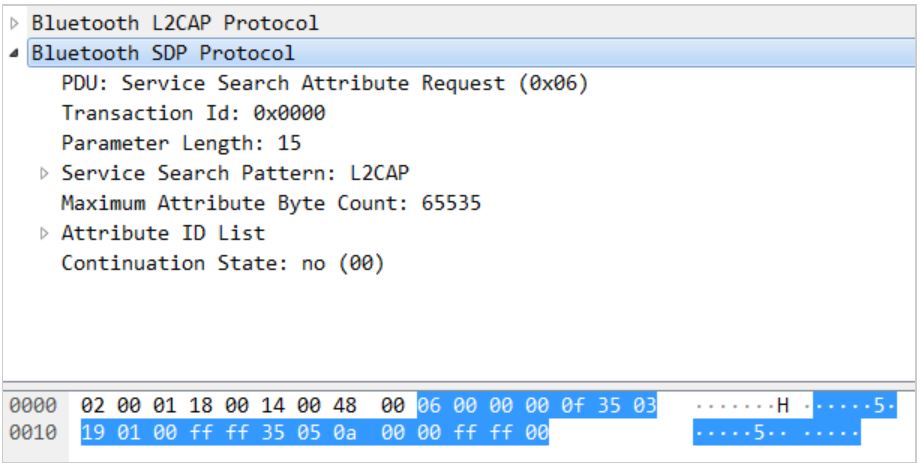
Image Source: 360
Out-of-bounds read exits in the (PDU=4) of function [SDPServerConnection handleServiceAttributeRequest:length:transactionID:] as CVE-2020-3847.
Affected Products:
macOS Catalina prior to 10.15.3
Advisory:
https://support.apple.com/en-in/HT210919
Mitigation:
Apple has updated the patch and released for CVE-2020-3847.
Qualys customers can scan their network with QID(s)# 372361 to detect vulnerable assets. Kindly continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources:
- https://blogs.360.cn/post/macOS_Bluetoothd_0-click.html
- https://support.apple.com/en-in/HT210919