Overview
Jenkins recently released updates for the critical memory corruption vulnerability (CVE-2019-17638) in the Jetty web server. Successful exploitation of this vulnerability may allow unauthenticated users to obtain sensitive information through HTTP response headers.
Jenkins is typically run as a standalone application in its own process with the built-in Java servlet container or application server (Jetty).
The vulnerability exists in the Jetty server versions from 9.4.27.v20200227 to 9.4.29.v20200521, which was introduced to handle large HTTP response headers and to prevent buffer overflows. In case of an HTTP response header that’s too large, these versions throw an exception to produce an HTTP 431 error. This leads to memory corruption and information disclosure.
Description
In the bug report of this vulnerability, the researcher says, “In case of too large response headers, Jetty throws an exception to produce an HTTP 431 error. When this happens, the ByteBuffer containing the HTTP response headers is released back to the ByteBufferPool twice. Because of this double release, two threads can acquire the same ByteBuffer from the pool and while thread1 is about to use the ByteBuffer to write response1 data, thread2 fills the ByteBuffer with response2 data. Thread1 then proceeds to write the buffer that now contains response2 data. This results in client1, which issued request1 and expects responses, to see response2 which could contain sensitive data belonging to client2 (HTTP session ids, authentication credentials, etc.).”
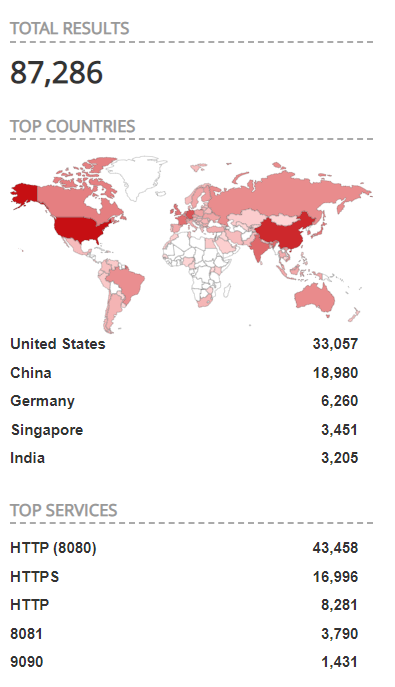
On Shodan, we observed more than 80,000 publicly available devices on the internet that may be vulnerable.
Image Source: Shodan
Remediation
This vulnerability has been fixed in Jetty 9.4.30.v20200611. The Jenkins has patched the flaw in Jenkins 2.243 and Jenkins LTS 2.235.5
Detection
Qualys customers can scan their network with QID 13949 to detect vulnerable assets. Kindly continue to follow Qualys Threat Protection for more coverage on these vulnerabilities.
References