The WannaDecrypt0r ransomware has infected at least 16 Hospitals in the UK and has been spreading quite a bit within the masses. The ransomware is being identified with many names such as WannaCrypt, WannaCry, WanaCrypt0r, WCrypt, WCRY and WannaDecrypt0r. At present, it is believed that over 36000 machines have been compromised by this ransomware. All pre Windows 10 operating systems are susceptible to this attack. The ransomware is reportedly using the ETERNALBLUE SMB exploit that was previously disclosed by the Shadow Brokers. Per MSRC, any machine patched with MS17-010 is protected from the vulnerability.
Infection:
The contents of the compromised machine are encrypted and the ransom for decryption is between $300 to $600 in Bitcoins. After a certain amount of time, there is a penalty and the fine increases. The WannaDecrypt0r also warns the user that all files will be deleted if they don’t pay up.
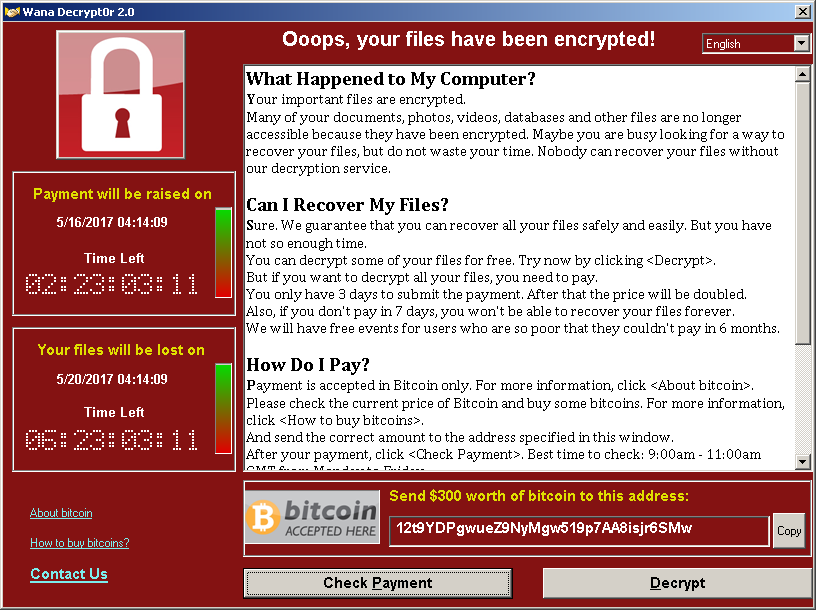
Once infected, the files are encrypted and any newly created files are promptly encrypted. All encrypted files have the extension of .WNCRY.
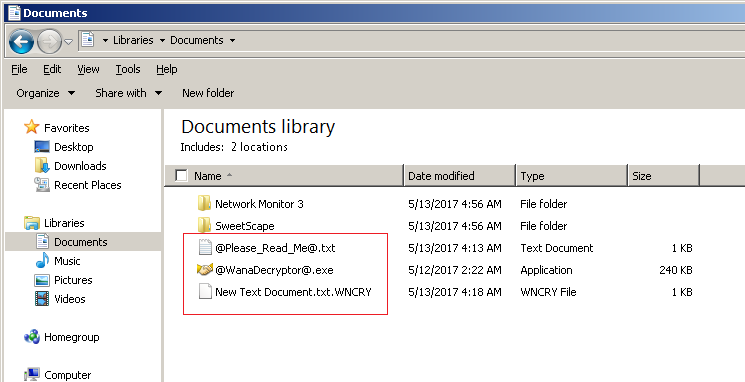
In the image above we can see: –
- .WNCRY encrypted file
- @WannDecrypt@.exe decryptor/ransom note
- @Please_Read_Me@.txt – Instructions for user to retrieve file and payment instructions.
This pattern is followed throughout. Every folder whose contents have been encrypted will contain @WannDecrypt@.exe and Please_Read_Me@.txt. Upon execution WannaDecrypt0r drops a bunch of files for its operations.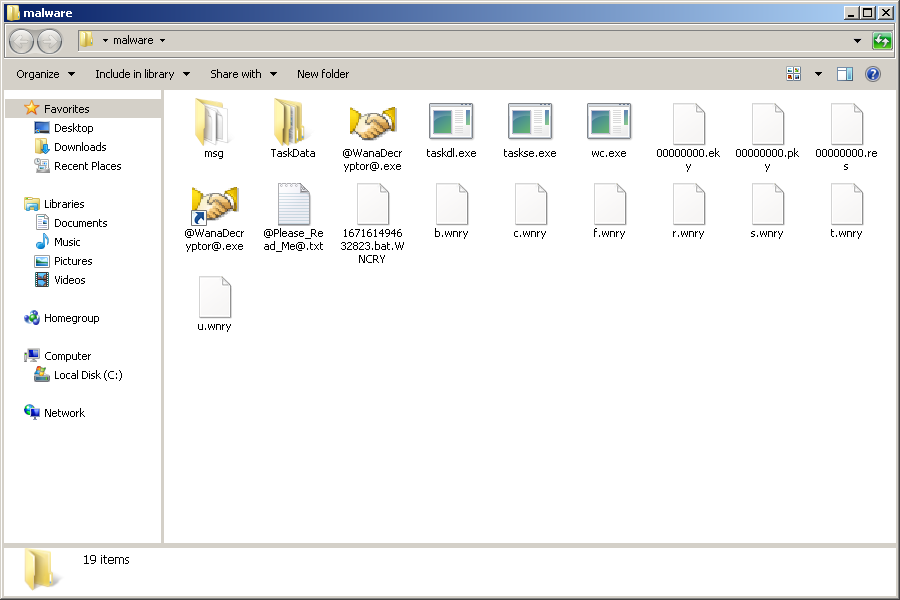
It also adds a registry entry HKLM\SOFTWARE\WanaCrypt0r with key wd with the path to its current working directory. A glance at the plain text string within the ransomware reveals 3 possible bitcoin wallets.
- 115p7UMMngoj1pMvkpHijcRdfJNXj6LrLn
- 12t9YDPgwueZ9NyMgw519p7AA8isjr6SMw
- 13AM4VW2dhxYgXeQepoHkHSQuy6NgaEb94
Mitigation:
We request organizations to scan their network with
- QID 91345 to detect a missing MS17-010 patch.
- QID 1029 to detect WannaDecrypt0r ransomware artifacts.
- QID 91360 for detecting ETERNALBLUE.
- QID 70077 for detecting DOUBLEPULSAR backdoors.
As a precaution we also suggest our customers to disable SMBv1. Please continue follow up on ThreatProtect for more information regarding this vulnerability.
Update:
Microsoft has released Security updates to address the SMB vulnerabilities in OS versions with custom support for Windows XP, Windows 8, and Windows Server 2003. In addition to the patch Microsoft has also released updates for Windows Defender to detect this threat as Ransom:Win32/WannaCrypt.