Summary:
Amidst the global pandemic time period, DHS CISA and FBI share list of top 10 most exploited vulnerabilities on May 12,2020. Department of Homeland Security Cybersecurity and Infrastructure Security Agency (DHS CISA) and the Federal Bureau of Investigation (FBI), urges organizations in the public and private sector to apply necessary updates in order to prevent the most common forms of attacks encountered today.
Description:
U.S. Government reporting has identified the top 10 most exploited vulnerabilities by state, nonstate, and unattributed cyber actors from 2016 to 2019 as follows:
– CVE-2017-11882
– CVE-2017-0199
– CVE-2017-5638
– CVE-2012-0158
– CVE-2019-0604
– CVE-2017-0143
– CVE-2018-4878
– CVE-2017-8759
– CVE-2015-1641
– CVE-2018-7600
Vulnerabilities Exploited in 2020
- Virtual Private Networks (VPNs)
- An arbitrary code execution vulnerability in Citrix VPN appliances, known as CVE-2019-19781, has been detected in exploits in the wild.
- An arbitrary file reading vulnerability in Pulse Secure VPN servers, known as CVE-2019-11510, continues to be an attractive target for malicious actors.
- March 2020 brought an abrupt shift to work-from-home that necessitated, for many organizations, rapid deployment of cloud collaboration services, such as Microsoft Office 365 (O365).
- Cybersecurity weaknesses—such as poor employee education on social engineering attacks and a lack of system recovery and contingency plans—have continued to make organizations susceptible to ransomware attacks in 2020.
- Vulnerable Products: Microsoft Office 2007 SP3/2010 SP2/2013 SP1/2016 Products
- Associated Malware: Loki, FormBook, Pony/FAREIT
- Mitigation: Update affected Microsoft products with the latest security patches
- More Detail: https://nvd.nist.gov/vuln/detail/CVE-2017-11882
- IOCs: https://www.us-cert.gov/ncas/analysis-reports/ar20-133e
- Vulnerable Products: Microsoft Office 2007 SP3/2010 SP2/2013 SP1/2016, Vista SP2, Server 2008 SP2, Windows 7 SP1, Windows 8.1
- Associated Malware: FINSPY, LATENTBOT, Dridex
- Mitigation: Update affected Microsoft products with the latest security patches
- More Detail: https://nvd.nist.gov/vuln/detail/CVE-2017-0199
- IOCs: https://www.us-cert.gov/ncas/analysis-reports/ar20-133g, https://www.us-cert.gov/ncas/analysis-reports/ar20-133h, https://www.us-cert.gov/ncas/analysis-reports/ar20-133p
- Vulnerable Products: Apache Struts 2 2.3.x before 2.3.32 and 2.5.x before 2.5.10.1
- Associated Malware: JexBoss
- Mitigation: Upgrade to Struts 2.3.32 or Struts 2.5.10.1
- More Detail: https://www.us-cert.gov/ncas/analysis-reports/AR18-312A, https://nvd.nist.gov/vuln/detail/CVE-2017-5638
CVE-2012-0158
- Vulnerable Products: Microsoft Office 2003 SP3, 2007 SP2 and SP3, and 2010 Gold and SP1; Office 2003 Web Components SP3; SQL Server 2000 SP4, 2005 SP4, and 2008 SP2, SP3, and R2; BizTalk Server 2002 SP1; Commerce Server 2002 SP4, 2007 SP2, and 2009 Gold and R2; Visual FoxPro 8.0 SP1 and 9.0 SP2; and Visual Basic 6.0
- Associated Malware: Dridex
- Mitigation: Update affected Microsoft products with the latest security patches
- More Detail: https://www.us-cert.gov/ncas/alerts/aa19-339a, https://nvd.nist.gov/vuln/detail/CVE-2012-0158
- IOCs: https://www.us-cert.gov/ncas/analysis-reports/ar20-133i, https://www.us-cert.gov/ncas/analysis-reports/ar20-133j, https://www.us-cert.gov/ncas/analysis-reports/ar20-133k, https://www.us-cert.gov/ncas/analysis-reports/ar20-133l, https://www.us-cert.gov/ncas/analysis-reports/ar20-133n, https://www.us-cert.gov/ncas/analysis-reports/ar20-133o
CVE-2019-0604
- Vulnerable Products: Microsoft SharePoint
- Associated Malware: China Chopper
- Mitigation: Update affected Microsoft products with the latest security patches
- More Detail: https://nvd.nist.gov/vuln/detail/CVE-2019-0604
CVE-2017-0143
- Vulnerable Products: Microsoft Windows Vista SP2; Windows Server 2008 SP2 and R2 SP1; Windows 7 SP1; Windows 8.1; Windows Server 2012 Gold and R2; Windows RT 8.1; and Windows 10 Gold, 1511, and 1607; and Windows Server 2016
- Associated Malware: Multiple using the EternalSynergy and EternalBlue Exploit Kit
- Mitigation: Update affected Microsoft products with the latest security patches
- More Detail: https://nvd.nist.gov/vuln/detail/CVE-2017-0143
- Vulnerable Products: Adobe Flash Player before 28.0.0.161
- Associated Malware: DOGCALL
- Mitigation: Update Adobe Flash Player installation to the latest version
- More Detail: https://nvd.nist.gov/vuln/detail/CVE-2018-4878
- IOCs: https://www.us-cert.gov/ncas/analysis-reports/ar20-133d
- Vulnerable Products: Microsoft .NET Framework 2.0, 3.5, 3.5.1, 4.5.2, 4.6, 4.6.1, 4.6.2 and 4.7
- Associated Malware: FINSPY, FinFisher, WingBird
- Mitigation: Update affected Microsoft products with the latest security patches
- More Detail: https://nvd.nist.gov/vuln/detail/CVE-2017-8759
- IOCs: https://www.us-cert.gov/ncas/analysis-reports/ar20-133f
CVE-2015-1641
- Vulnerable Products: Microsoft Word 2007 SP3, Office 2010 SP2, Word 2010 SP2, Word 2013 SP1, Word 2013 RT SP1, Word for Mac 2011, Office Compatibility Pack SP3, Word Automation Services on SharePoint Server 2010 SP2 and 2013 SP1, and Office Web Apps Server 2010 SP2 and 2013 SP1
- Associated Malware: Toshliph, UWarrior
- Mitigation: Update affected Microsoft products with the latest security patches
- More Detail: https://nvd.nist.gov/vuln/detail/CVE-2015-1641
- IOCs: https://www.us-cert.gov/ncas/analysis-reports/ar20-133m
- Vulnerable Products: Drupal before 7.58, 8.x before 8.3.9, 8.4.x before 8.4.6, and 8.5.x before 8.5.1
- Associated Malware: Kitty
- Mitigation: Upgrade to the most recent version of Drupal 7 or 8 core.
- More Detail: https://nvd.nist.gov/vuln/detail/CVE-2018-7600
Discover Exploitable Vulnerabilities using Qualys VMDR
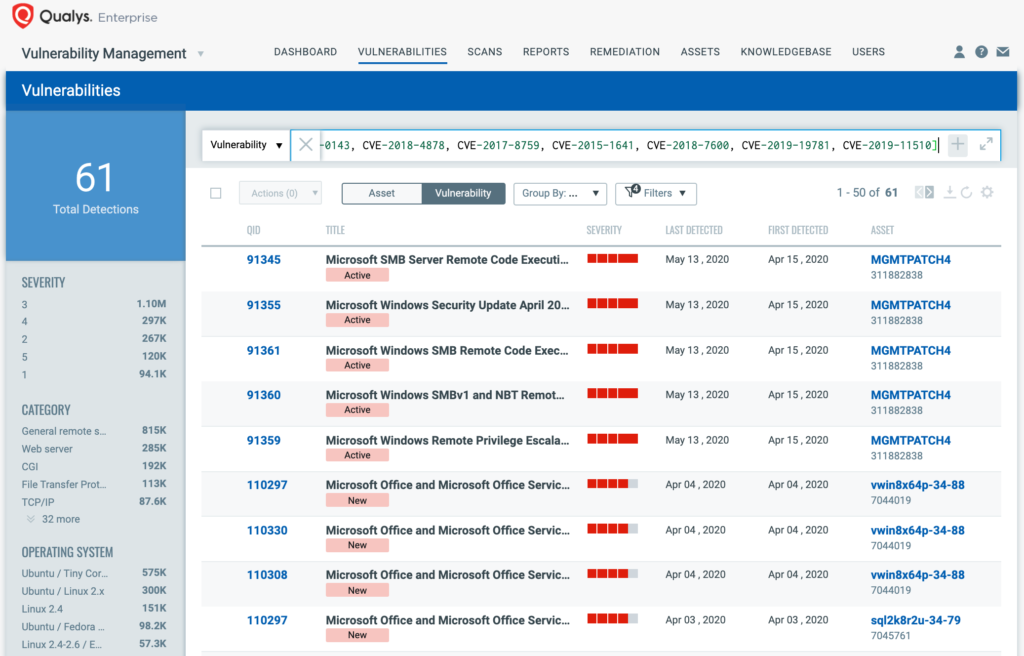
You can see all your impacted hosts for exploitable vulnerabilities in vulnerabilities view by using QQL query:
vulnerabilities.vulnerability.cveIds:[CVE-2017-11882, CVE-2017-0199, CVE-2017-5638, CVE-2012-0158, CVE-2019-0604, CVE-2017-0143, CVE-2018-4878, CVE-2017-8759, CVE-2015-1641, CVE-2018-7600, CVE-2019-19781, CVE-2019-11510]
This will return a list of all impacted hosts.
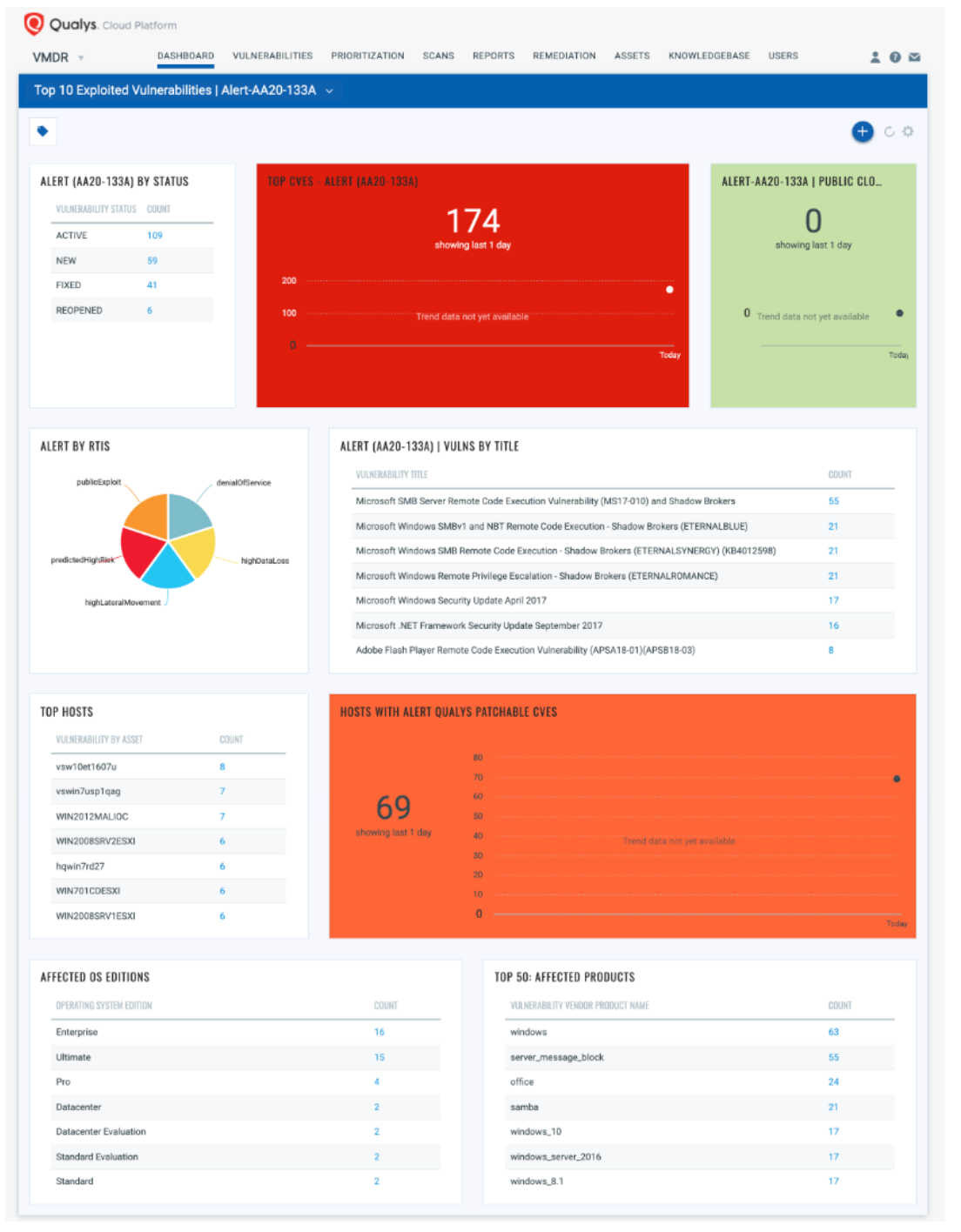
With VM Dashboard, you can track most exploitable CVEs in recent times, along with impacted hosts, their status and overall management in real time. With trending enabled for dashboard widgets, you can keep track of vulnerability trends in your environment using Top 10 Routinely Exploited Vulnerabilities Dashboard –
Mitigations for Vulnerabilities Exploited in 2020
CVE-2019-11510
- Vulnerable Products: Pulse Connect Secure 9.0R1 – 9.0R3.3, 8.3R1 – 8.3R7, 8.2R1 – 8.2R12, 8.1R1 – 8.1R15 and Pulse Policy Secure 9.0R1 – 9.0R3.1, 5.4R1 – 5.4R7, 5.3R1 – 5.3R12, 5.2R1 – 5.2R12, 5.1R1 – 5.1R15
- Mitigation: Update affected Pulse Secure devices with the latest security patches.
- More Detail:
- Vulnerable Products: Citrix Application Delivery Controller, Citrix Gateway, and Citrix SDWAN WANOP
- Mitigation: Update affected Citrix devices with the latest security patches
- More Detail:
- https://www.us-cert.gov/ncas/alerts/aa20-020a
- https://www.us-cert.gov/ncas/alerts/aa20-031a
- https://www.fireeye.com/blog/products-and-services/2020/01/fireeye-and-citrix-tool-scans-for-iocs-related-to-vulnerability.html
- https://nvd.nist.gov/vuln/detail/CVE-2019-19781
- https://www.microsoft.com/security/blog/2020/04/28/ransomware-groups-continue-to-target-healthcare-critical-services-heres-how-to-reduce-risk/
Oversights in Microsoft O365 Security Configurations
- Vulnerable Products: Microsoft O365
- Mitigation: Follow Microsoft O365 security recommendations
- More Detail: https://www.us-cert.gov/ncas/alerts/aa20-120a
Organizational Cybersecurity Weaknesses
- Vulnerable Products: Systems, networks, and data
- Mitigation: Follow cybersecurity best practices
- More Detail: https://www.cisa.gov/cyber-essentials
Qualys customers have been supported and protected against these whole list of exploits and vulnerabilites as and when required.
Qualys customers can scan their network with QID(s)# 110308,91364,91355,110297,87305,370555,216122,216121,150175,11779,316096,316095,150173,11771,90793,110330,91361,91360,91359,91347,91345,236636,100328,370756,91410,110252,371954,150218,277288,176337,11942,150273,372305,38771 to detect vulnerable assets. Many of them already have a ThreatProtect blogs which are hyperlinked to the respective CVEs. Kindly continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.