On Friday, April 14, 2017 – The mysterious hacking group ShadowBrokers released over 300MB of NSA hacking tools and exploits. The dump is hosted as a Yandex disk with password “Reeeeeeeeeeeeeee”. The current dump contains 3 folders oddjob, windows, swift as described below, and a detailed list of the contents can be found here.
| oddjob | An implant builder |
| windows | Exploits, supporting resources and exploit framework similar to Metasploit |
| swift | SQL scripts for querying SWIFT data from databases |
Most of the windows exploits are organized in a 3 file system .exe, .fb and .xml file. The .fb file lists the options supported by the exploit, and the XML file is used as a configuration file for the exploit.
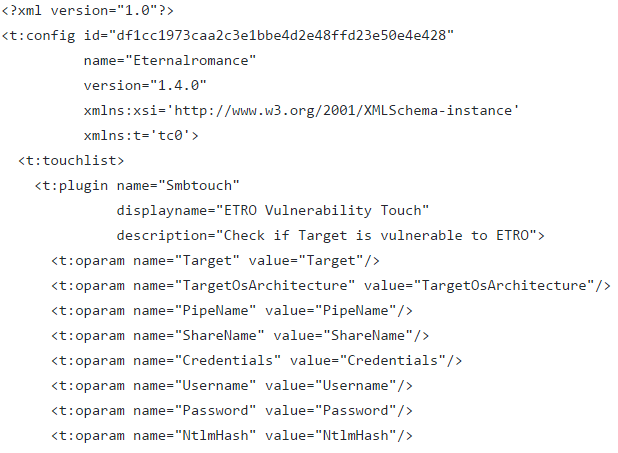
The .fb file listing options supported by ETERNALROMANCE are:
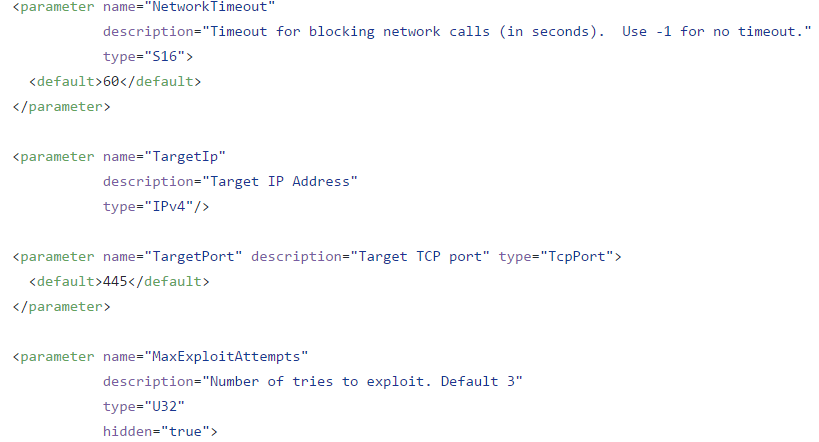
Below are some of the exploits that are in the spotlight and/or have been successfully tested. This list will be updated as we investigate further .
| Exploit | Description | Path |
|---|---|---|
| ETERNALROMANCE (MS17-010) | SMBv1 Exploit Targeting Windows XP, 2003 SP1 SP2, 2008* SP1 SP2, 2008 R2* SP1, Vista SP1 SP2 , 7 SP1 | shadowbrokers-exploits/windows/exploits/ |
| ETERNALCHAMPION (MS17-010) | SMBv1/v2 exploit Windows XP SP1 SP2, 7 SP1, 2003 SP1 SP2, 2008* SP1 SP2, 2008 R2* SP1, Vista SP1 SP2, 8 | shadowbrokers-exploits/windows/specials/ |
| ETERNALBLUE (MS17-010) | SMBv2 exploit Targeting Windows XP SP1 SP2 SP3, 7 SP1, 2003 SP1 SP2, 2008* SP1 SP2, 2008 R2* SP1, Vista SP1 SP2 | shadowbrokers-exploits/windows/specials/ |
| EXPLODINGCAN | Exploit targeting CVE-2017-7269 on Windows 2003 SP1 SP2 | shadowbrokers-exploits/windows/exploits/ |
| EWOKFRENZY | Lotus Domino 6.5.4, 7.0.2 | shadowbrokers-exploits/windows/exploits/ |
| ZIPPYBEER | Microsoft Domain Controller exploit | shadowbrokers-exploits/windows/exploits/ |
| ESTEEMAUDIT | DLL Injection exploit via RDP Targeting Windows XP SP1,SP2,SP3; Windows 2003 SP1,SP2 | shadowbrokers-exploits/windows/exploits/ |
| EASYBEE | MDaemon WebAdmin Exploit | shadowbrokers-exploits/windows/exploits/ |
| ENGLISHMANSDENTIST | Probable Outlook WebAccess Exploit | shadowbrokers-exploits/windows/exploits/ |
| ERRATICGOPHER | SMBv1 Exploit targeting Windows 2000 SP4,XP SP2 SP3,2003 SP1 SP2 | shadowbrokers-exploits/windows/exploits/ |
| ESKIMOROLL (MS14-068) | Kerberos Service exploit targeting Windows 2000,2003,2003 R2,2008,2008 R2 | shadowbrokers-exploits/windows/exploits/ |
| ETERNALSYNERGY (MS17-010) | SMBv1 Exploit targeting Windows 8,2012 | shadowbrokers-exploits/windows/exploits/ |
| EMPHASISMINE | Exploit targeting Lotus Domino 6.5.4-6.5.5FP1, 7.0-8.5.2 | shadowbrokers-exploits/windows/exploits/ |
| EMRALDTHREAD (MS10-061) | Exploit targeting SMBv1 on Windows XP SP1 SP2 SP3, 2003 SP1 SP2 | shadowbrokers-exploits/windows/exploits/ |
| EDUCATEDSCHOLAR (MS09-050) | Exploit targeting SMBv1 on Windows Vista SP1 SP2, 2008 SP1 SP2 | shadowbrokers-exploits/windows/exploits/ |
| ECLIPSEDWING | Exploit targeting Server service on Windows 2000 all versions, XP SP1-SP3, 2003 SP1 SP2 | shadowbrokers-exploits/windows/exploits/ |
| EASYPI | Exploit targeting Lotus ccMail on Windows NT, 200, XP, 2003 | shadowbrokers-exploits/windows/exploits/ |
* We are in the process of verifying if the exploit works for this platform
FUZZBUNCH:
Fuzzbunch is an exploitation framework similar to Metasploit that is used to run exploits against target machines. The framework is executed via fb.py. The framework requires python 2.6 to function, later versions of python seem to fail due a dependency on python26.dll in one of the .pyd files. Fuzzbunch is compatible on 32- and 64-bit architectures. It provides a console-based interface for collecting exploit configuration.
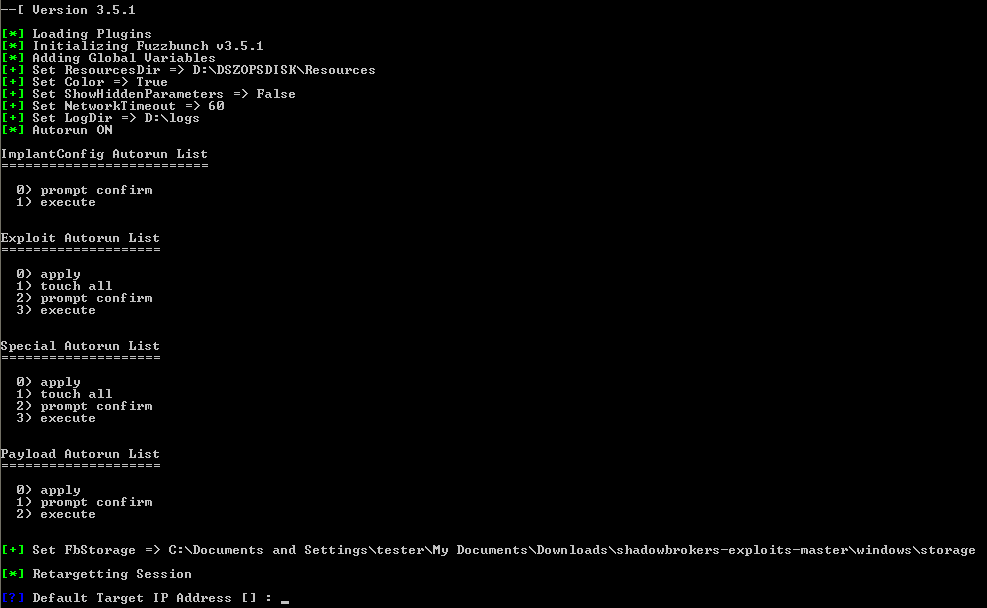
Upon selecting an exploit Fuzzbunch automatically collects information about the targets and parameters for the exploit.
DanderSpritz:
A command & control tool used for post exploitation monitoring and controlling. The tool provides utilities for generating payloads in form of dll’s and exe’s for injection into target machines processes among other things.
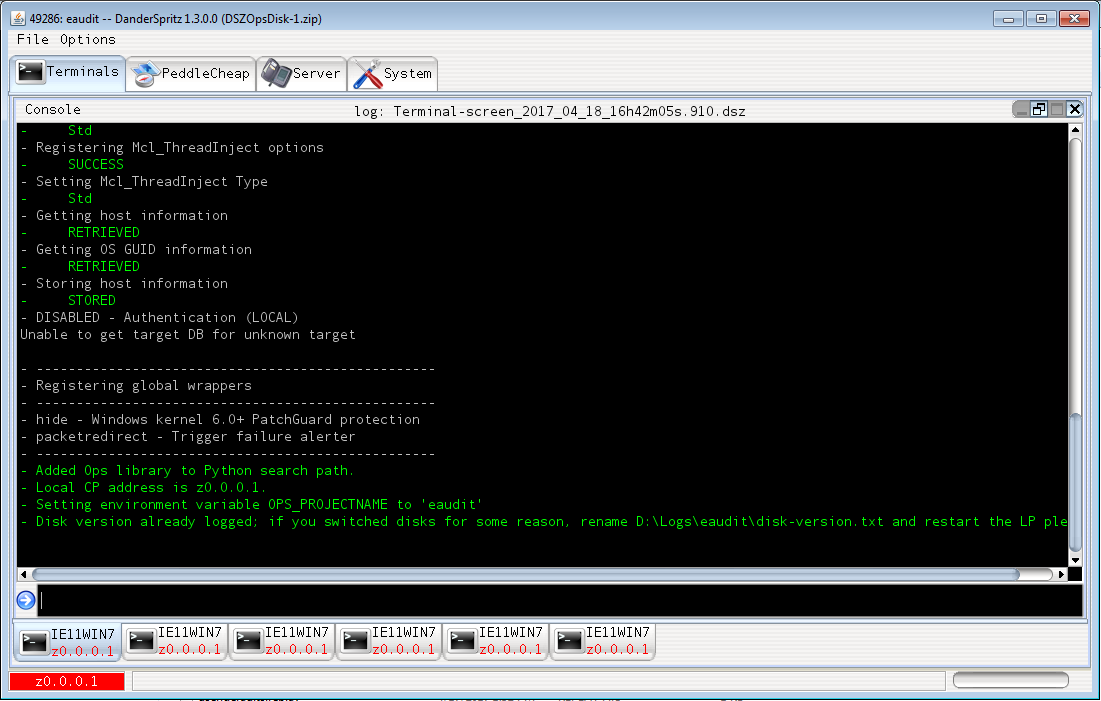
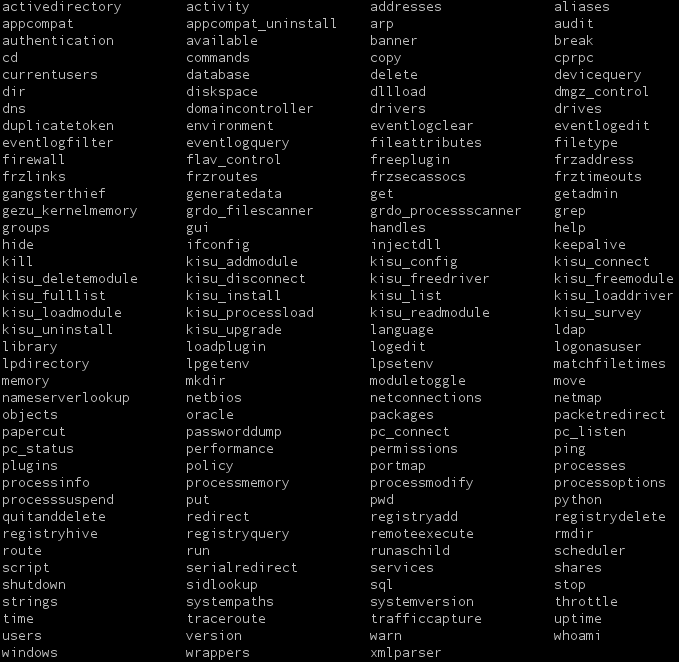
Below are the supported commands.
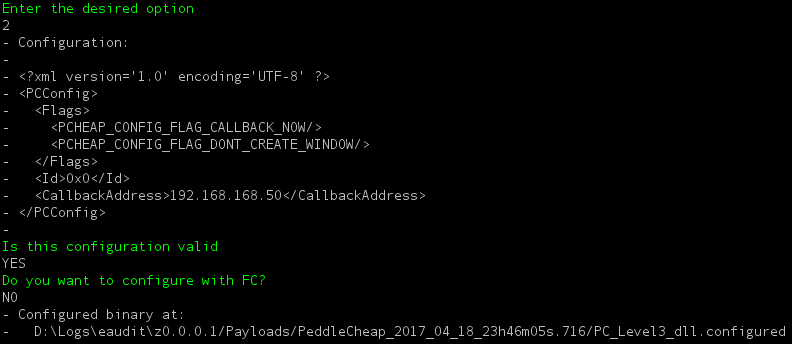
As mentioned earlier the tool is also used to generate payloads to use with Doublepulsar.
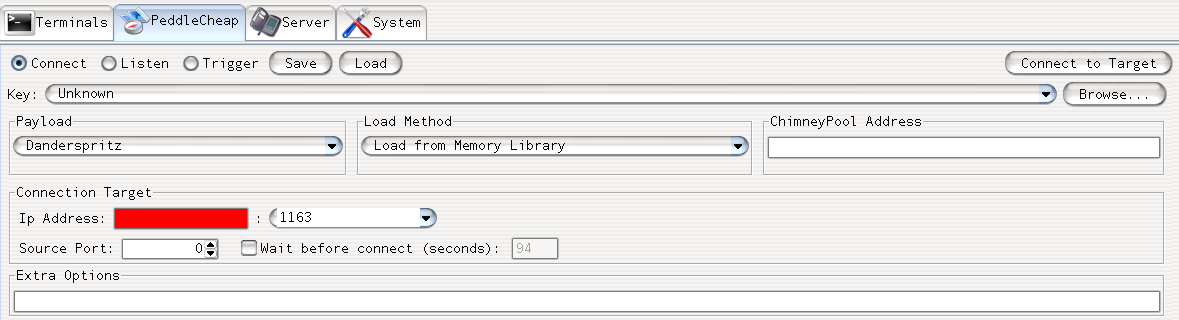
DanderSpritz ships with module PeddleCheap used to connect and listen to target machine. It can also be used to trigger exploits on target machines.
MSRC Update:
The Microsoft Security Response Center (MSRC) has released a statement addressing the exploits released by ShadowBrokers. MSRC has assured us that most of the exploits are already patched. In addition to the ones listed below some of the exploits do not reproduce on supported platforms, therefore customers running Windows 7 and latest versions of Windows or Exchange Server 2010 (EnglismansDentist) are not vulnerable.
| Exploit | Patch |
|---|---|
| EternalBlue | Addressed by MS17-010 |
| EmeraldThread | Addressed by MS10-061 |
| EternalChampion | Addressed by CVE-2017-0146 & CVE-2017-0147 |
| ErraticGopher | Addressed prior to the release of Windows Vista |
| EsikmoRoll | Addressed by MS14-068 |
| EternalRomance | Addressed by MS17-010 |
| EducatedScholar | Addressed by MS09-050 |
| EternalSynergy | Addressed by MS17-010 |
| EclipsedWing | Addressed by MS08-067 |
Conclusion:
Based on our initial analysis many exploits appear to be zero-day vulnerabilities, i.e. issues where there are no patches from the vendor. In addition to that, many exploits affect end-of-life software for which vendors will not release patches. A good mitigation step is to disable SMB service as many exploits are targeting various versions of SMB. We request organizations to keep track of patches released by the respective vendors and upgrade their end-of-life software.
Update:
An update for the Metasploit framework adds a new more reliable exploit for EternalRomance, EternalChampion, EternalSynergy. If successful an attacker can target machines listed below.
| Operating System | Versions/Service Pack/Build Versions | Architecture |
| Windows 2000 | SP0,Professional SP4,Advanced Server SP4 | x86 |
| Windows XP | SP0,SP1,SP2,SP3 | x86 |
| Windows XP | SP2 | x64 |
| Windows Vista | Home Premium | x86 |
| Windows Vista | x64 | |
| Windows 7 | Ultimate SP1, Enterprise SP1 | x86 |
| Windows 7 | SP0,SP1 | x64 |
| Windows 8 | x86,x64 | |
| Windows 8.1 | Enterprise Evaluation 9600,SP1 | x86 |
| Windows 8.1 | SP1 | x64 |
| Windows 8.1 | x64 | |
| Windows 10 | Enterprise 10.10240,10.10586,10.0.14393 | x86 |
| Windows 10 | Enterprise Evaluation 10.14393 10.0.14393,10.10586 | x64 |
| Windows Server 2003 | SP0,SP1, Enterprise SP2,R2 SP1,R2 SP2 | x86 |
| Windows Server 2003 | SP1,R2 SP1,R2 SP2 | x64 |
| Windows Server 2008 | SP1 | x86 |
| Windows Server 2008 | R2,R2 SP1 | x64 |
| Windows Server 2008 | x64 | |
| Windows Server 2008 R2 | x64 | |
| Windows Server 2008 R2 | SP1 | x64 |
| Windows Server 2012 | x64 | |
| Windows Server 2012 | R2,R2 Standard 9600,R2 SP1 | x64 |
| Windows Server 2012 R2 | x86 | |
| Windows Server 2016 | 10.10586,Data Center 10.14393 | x64 |
References:
ShadowBrokers Dump
Lost in Translation
MSRC Statement
EclipsedWing MS087-067 is missing please include them also
Thanks for catching that. Updated to include EclipsedWing