In our previous post we have seen how the the initial WannaCry executable configures the target system and creates the tasksche.exe file under C:\WINDOWS directory and executes it with command line argument /i. In this post we will continue our analysis to see what this process is upto.
| MD5 | 84C82835A5D21BBCF75A61706D8AB549 |
| SHA-1 | 5FF465AFAABCBF0150D1A3AB2C2E74F3A4426467 |
| FileDescription | DiskPart |
| OriginalFilename | diskpart.exe |
Upon execution tasksche.exe obtains the NetBios name of the target , it uses this string to generate a seed value for srand and rand functions, which is further used to generate a random string. We will see later what this value is used for. In our case the NetBios name IEUSER leads to “midtxzggq900”.
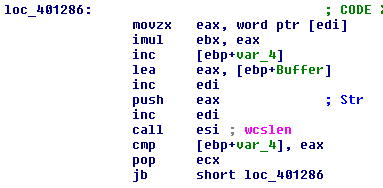
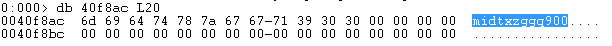
Next it changes its current directory to C:\ProgramData\, and uses the random string to create a directory under C:\ProgramData\midtxzggq900.
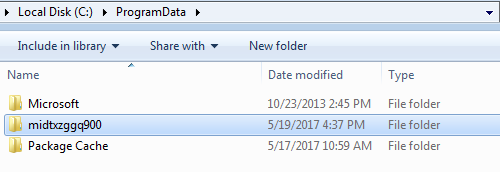
it copies tasksche.exe from C:\Windows\tasksche.exe to this location.
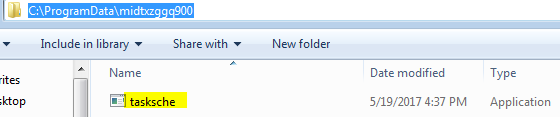
Next it tries to create a service with the name midtxzggq900 if it is not present and sets the executable path to cmd.exe /c “C:\ProgramData\midtxzggq900\tasksche.exe. To continue our analysis we will need to track this process.
This new process changes the current directory to C:\ProgramData\midtxzggq900. It creates a registry entry under HKLM\Software with the display name WanaCrypt0r. It creates a key named wd with value C:\ProgramData\midtxzggq900. Point to note is the operations so far are not malicious, creating registry entries are normal even for legitimate applications. What they used it for is a whole different story.
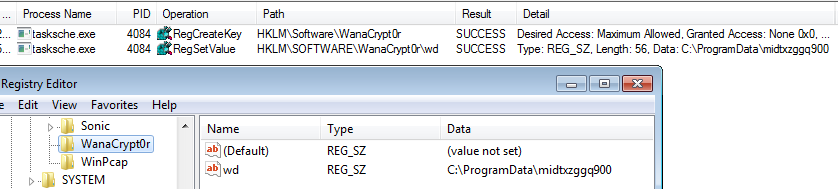
After successfully creating the registry entries it looks within its resource section. We see a similar behavior in the initial WannaCry executable. It tries to find resource ID 2058 under resource block “XIA”.
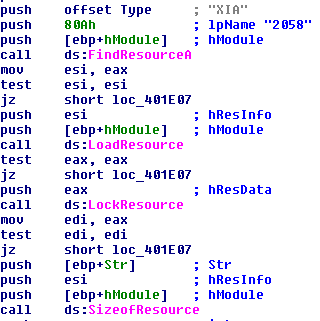
This entry contains a file with header “PK”. This is indicative of a zipped file format. So we save this section as a .zip file and try to unzip it, and it requires a password to proceed further. This is good it means that tasksche.exe will try to unzip this file somewhere.
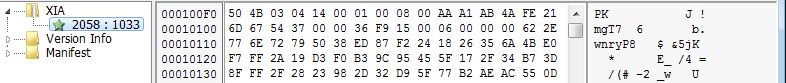
For a zip file we don’t need to extract its contents to view the files within. The file list of a zip file are stored in plain text and it can be extracted even without the password to the actual zip file. The zip contains .wnry, .exe files and a list files with language names as part of their file names, they could be ransom notes in different languages. The ransomware unzips the file with the password WNcry@2ol7. be unzipped is “b.wnry”. It first creates an empty file if it does not exist and proceeds to copy the contents into the new file. After creating the file it writes the contents after extracting it from taskche.exe. In a similar fashion all the files are unzipped and saved in the current working directory.
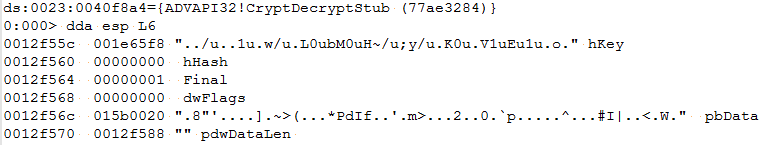
Now the ransomware tries to open c.wnry with in rb mode and reads 780 bytes . The file c.wnry contains the following .onion domains.
- gx7ekbenv2riucmf.onion
- 57g7spgrzlojinas.onion
- xxlvbrloxvriy2c5.onion
- 76jdd2ir2embyv47.onion
- cwwnhwhlz52maqm7.onion
- https://dist.torproject.org/torbrowser/6.5.1/tor-win32-0.2.9.10.zip
A cursory look at the plain text string of the executable also reveals the hard coded bitcoin wallets.
- 13AM4VW2dhxYgXeQepoHkHSQuy6NgaEb94
- 12t9YDPgwueZ9NyMgw519p7AA8isjr6SMw
- 115p7UMMngoj1pMvkpHijcRdfJNXj6LrLn
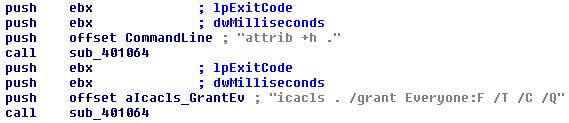
It tries to execute attrib +h this command sets the hidden file attribute, it is executed via CreateProcessA() with the CREATE_NO_WINDOW creation flag. Next it executes the icacls utility, this tool is used to display or modify the the Discretionary Access Control Lists(DACLs) of a machine. The command executed here is icacls . /grant Everyone:F /T /C /Q this grants full access to the files and the files within the subdirectories. The /c and /q ensure that this operation continues in spite of errors and suppresses success messages.
Now that all the files are setup and have full access, the ransomware resolves the addresses for crypto functions and file functions. It starts by reading 8 bytes from t.wnry which is a string WANACRY!, then 4 byte more 00 01 00 00 and the 100h bytes after that represents the encrypted AES key. This key is decrypted using the public AES key. The decrypted key is used to decrypt the rest of the file.
Once it is fully decrypted the resulting file is a PE executable with a DOS header. Lets dump the memory containing this file and take a look.
| MD5 | 7D36A6AA8CB6B504EE9213C200C831EB8D4EF26B |
| SHA-1 | 7D36A6AA8CB6B504EE9213C200C831EB8D4EF26B |
| File Type | Microsoft Visual C++ 6.0 DLL |
| FileDescription | Latvia Keyboard Layout |
| InternalName | kbdlv (3.13) |
| OriginalFilename | kbdlv.dl |
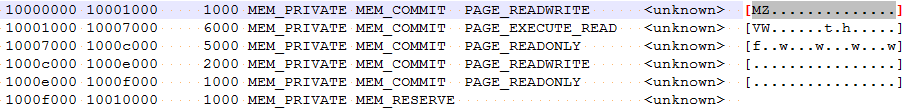
The file in question seems to be a .dll file with only one export entry TaskStart. We can expect to see a call to this function. Once the file is decrypted it allocates 64KB within the process memory space and writes the contents of the decrypted dll to this location. The allocated memory has R/W and execute permission.
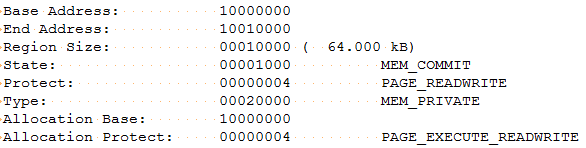
Now that the DLL has been saved in the process memory space, the ransomware will call the DLLEntryPoint code to initialize it.
After initializing the DLL it will proceed to resolve the address for TaskStart and call it. The first thing TaskStart does is to create a mutex MsWinZonesCacheCounterMutexA. Please refer to our ThreatProtect blog for more details about how the ransomware uses this mutex. After the mutex is the ransomware will execute taskkill.exe to terminate the following processes.
- taskkill.exe /f /im mysqld.exe
- taskkill.exe /f /im sqlwriter.exe
- taskkill.exe /f /im sqlserver.exe
- taskkill.exe /f /im MSExchange*
- taskkill.exe /f /im Microsoft.Exchange.*
It then proceeds to execute taskdl.exe. This executable deletes temporary files within each drive searching for files with .WNCRYT extension. Once these files have been deleted the ransomware makes a copy of u.wnry and renames it as @WanaDecryptor@.exe. Then it proceeds to create a .bat which consists of the code shown below. This batch file creates a shortcut to @WanaDecryptor@.exe
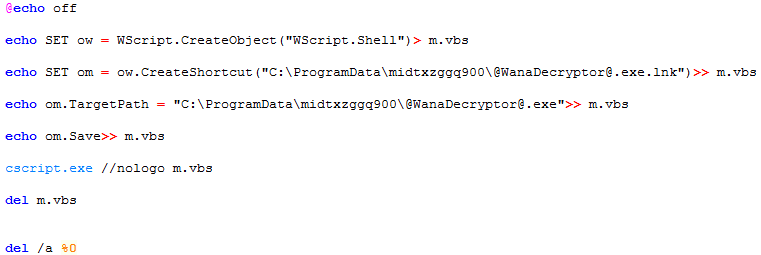
After this it creates a file named “@Please_Read_Me@.txt” this contains the ransom note with the amount bitcoins needed to decrypt the files and rudimentary instructions for payment. Next It obtains the paths to Desktop, Documents and enumerates all the files currently present and encrypts them by executing @WanaDecryptor@.exe. This executable will run the following console commands.
- cmd.exe /c vssadmin delete shadows /all /quiet &
- wmic shadowcopy delete &
- bcdedit /set {default} bootstatuspolicy ignoreallfailures &
- bcdedit /set {default} recoveryenabled no &
- wbadmin delete catalog -quiet
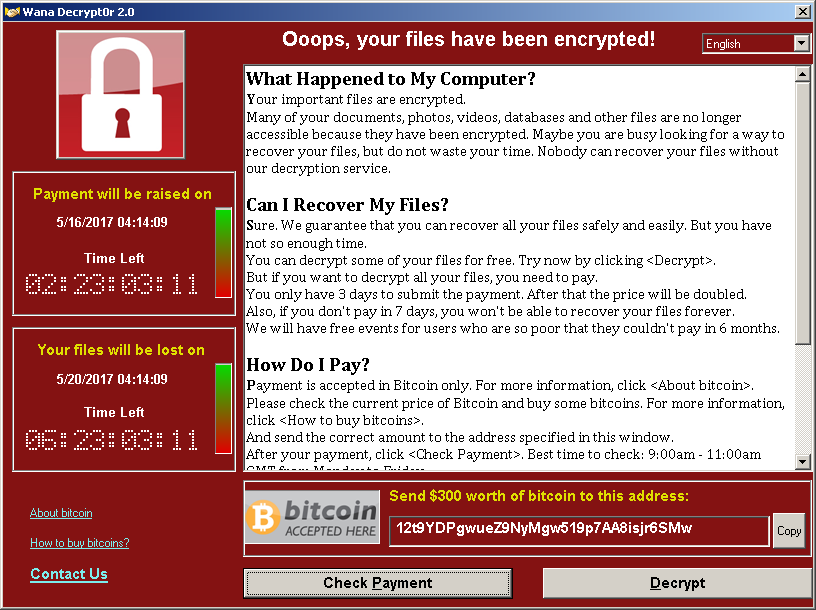
It will try to connect to the C&C service via Tor. If the payment is made it can verify the same. This is a GUI application with a window named Wana Decrypt0r 2.0.
After compromising the machine the ransom-ware tries to spread to other machine on the network. We will try to have a look at this in a separate post.
Summary:
To sum up upon execution WannaCry checks if it can reach certain dummy domains as sandbox detection and proceeds if the check fails. It extracts a secondary executable (tasksche.exe) embedded within its resource section. The extracted executable generates a random string based on the current machines NetBios name and creates a directory under C:\ProgramData and a service with the same name. It further extracts a zipped file from it resource section. The zipped file contains all the necessary data required for the ransomware to generate its AES encryption keys. it Decrypts t.wnry to reveal a dll which will be injected into the current running process. This dll performs the bulk of the crypto operations.
Conclusion:
The effectiveness of the WannaCry ransom-ware shows the staggering number of public facing unpatched, EOL operating systems. This prompted Microsoft to issue emergency patches for EOL. All the samples that were caught in the wild refer to the same 2 bitcoin wallets, which shows that there is no way for the ransomware admins to recognize from whom the payments were received. WannaCry depends on EternalBlue to spread to other networks. So it very crucial for organizations to patch their machines with Ms17-017 to address SMB vulnerabilities. Qualys QID 91360,91345, 70077 will detect vulnerable machines